
Deploying a next-gen cloud-native security information and event management (SIEM) in your security operations center (SOC) is a big step in the right direction toward significantly improving your organization’s security capabilities.
But once you have that state-of-the-art SIEM in your SOC, how do you get the most out of it? One key step is building and executing specific SIEM use cases designed to meet the particular needs of your organization. This post will cover:
- What is a use case?
- Benefits of a use case-driven approach
- Steps to creating better use cases for your SIEM
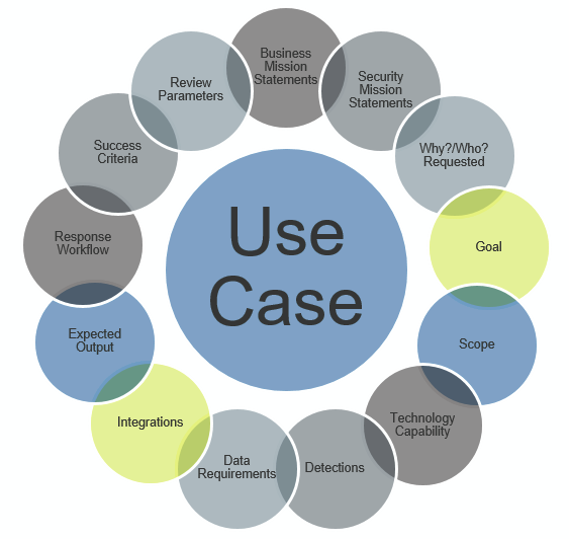
What Is a Use Case?
Before we dig into the details, let’s define what we mean by a use case. We’ll start by defining three interrelated types of use cases:
- A business use case is a need identified by senior managers. In the context of SIEM or security, it most often correlates with a security use case that identifies the technical/security need.
- A security use case is a technical or security need that supports business use case goals and objectives.
- A SIEM use case is a technical or security need identified by the SOC team to support business and security goals. For example, the SOC team could create and execute use cases around user and entity behavior analytics.
Security use cases are designed to mitigate business risks, improve processes or technology, or facilitate people-related improvements. Security use cases map to business use cases either directly or indirectly and can have a one-to-many or many-to-one relationship.
Using the security use case as a starting point, the SOC team creates a SIEM use case, which encompasses a technical or security need that supports both business and security goals. It is often quite similar — and frequently identical — to a security use case. Security use cases will often include a broader definition that encompasses several departments or business units, whereas the SIEM use case identified and executed by the SOC team is very specific and tactical. As an example, cybersecurity analytics is an area that lends itself to valuable use cases for SOC teams.
Benefits of a Use Case-Driven Approach
There are several benefits SOC teams will realize from taking a use case-driven approach when it comes to evaluating and building out your SIEM solution. They include:
- Accelerating time to value. Creating and executing specific use cases will reduce the amount of time spent implementing SIEM-related activities while demonstrating measurable value to key stakeholders on the broader security team and among senior management.
- Reducing analyst fatigue. Every SOC team strives to reduce false-positive alerts while also achieving quicker and more decisive mean time to detection (MTTD), mean time to response (MTTR), and mean time to contain (MTTC) the threats that matter most to their business.
- Improving SOC/incident response efficiency. Developing and executing on a well-thought-out SIEM use case will maximize the features in existing SOC products and help SOC analysts stop “chasing the impossible” while operating more effectively and efficiently.
- Improving the organization’s security posture. When SOC teams are able to focus on improvements and refinements to how they work — while spending less time fighting fires — it maximizes their visibility into the organization’s threat landscape.
- Complimenting personnel development frameworks. Well-crafted use cases, in addition to supporting important business needs, also emphasizes the purpose of their work to security personnel. This contributes to a better understanding of each team member’s development plan. This creates a stronger, more capable team and improves organizational security. For example, here are three SOC automation use cases that can help reduce analyst burnout.
5 Steps to Build More Effective SIEM Use Cases
To wrap up this post, we’ll leave you with these steps you can follow to build more effective SIEM use cases for your organization.
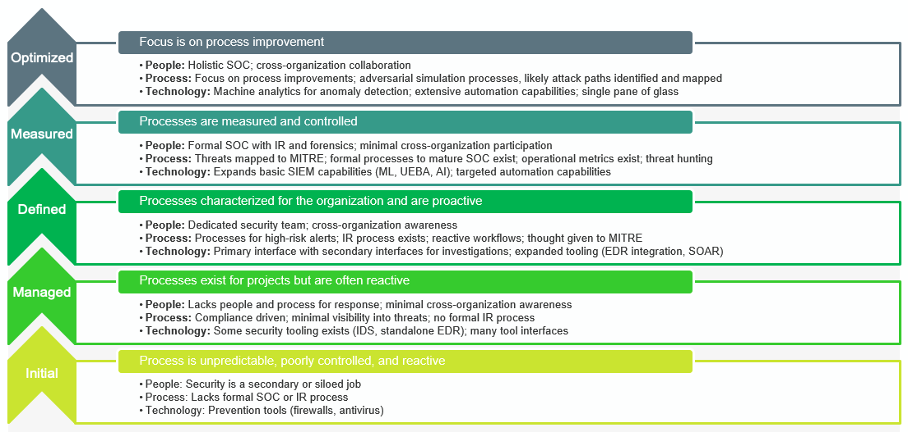
- Understand where you are on the maturity model vs. where you want to be.
- Clearly define your use case goals and objectives.
- Establish clear success criteria that will enable the team to know when they have accomplished goals or if additional work is needed.
- Implement and tune each use case until it is in the best possible place.
- Establish a roadmap and follow through to measure effectiveness.
By following these steps, your security team will be well on its way to getting the most out of its SIEM while also meeting business and security objectives.
Frequently Asked Questions
Some common SIEM use cases include:
- Threat Detection and Incident Response: SIEM platforms help organizations detect and respond to security threats in real-time by correlating and analyzing security event data from multiple sources, such as firewalls, intrusion detection systems (IDS), antivirus solutions, and network devices. By monitoring for suspicious activities and anomalies, SIEM solutions can alert security teams to potential security incidents, enabling prompt investigation and response.
- Log Management and Analysis: SIEM systems collect and centralize log data generated by IT systems, applications, and devices throughout the organization. This allows security teams to efficiently search, analyze, and investigate security events and incidents, aiding in forensic analysis, compliance reporting, and troubleshooting.
- Compliance and Regulatory Requirements: SIEM platforms play a crucial role in helping organizations meet compliance requirements and regulatory standards, such as GDPR, HIPAA, PCI DSS, and SOX. By collecting and analyzing security event data, SIEM solutions provide organizations with the visibility and audit trails necessary to demonstrate compliance with security policies and regulations.
- User Activity Monitoring: SIEM systems can monitor user activity and behavior across IT systems and applications, helping organizations detect insider threats, unauthorized access, and suspicious user behavior. By correlating user activity logs with other security event data, SIEM solutions can identify potential security risks and enforce access controls and policies.
- Threat Intelligence Integration: SIEM platforms often integrate with external threat intelligence feeds, allowing organizations to enrich security event data with contextual information about known threats, malicious IP addresses, and indicators of compromise (IOCs). By leveraging threat intelligence, SIEM solutions can enhance threat detection capabilities and improve the accuracy of security alerts.
- Anomaly Detection: SIEM systems use machine learning algorithms and statistical analysis to identify abnormal patterns and deviations from baseline behavior within the IT environment. By detecting anomalies in network traffic, user behavior, and system activity, SIEM solutions can alert security teams to potential security threats, such as insider threats, malware infections, or data exfiltration attempts.
- Incident Forensics and Investigation: SIEM platforms provide valuable forensic capabilities for investigating security incidents and breaches. By aggregating and correlating security event data from disparate sources, SIEM solutions enable security teams to reconstruct the timeline of events, trace the root cause of incidents, and gather evidence for incident response and remediation.
Given that every organization has unique security needs and resource constraints, users might be interested in understanding how to effectively identify and prioritize SIEM use cases that will provide the most immediate benefit to their security posture and business objectives.
Implementing SIEM use cases can come with its own set of challenges, including technical difficulties, alignment with business goals, or resource limitations. Users might be curious about these potential hurdles and seek advice on how to navigate them effectively to ensure successful implementation and optimization of their SIEM system.




