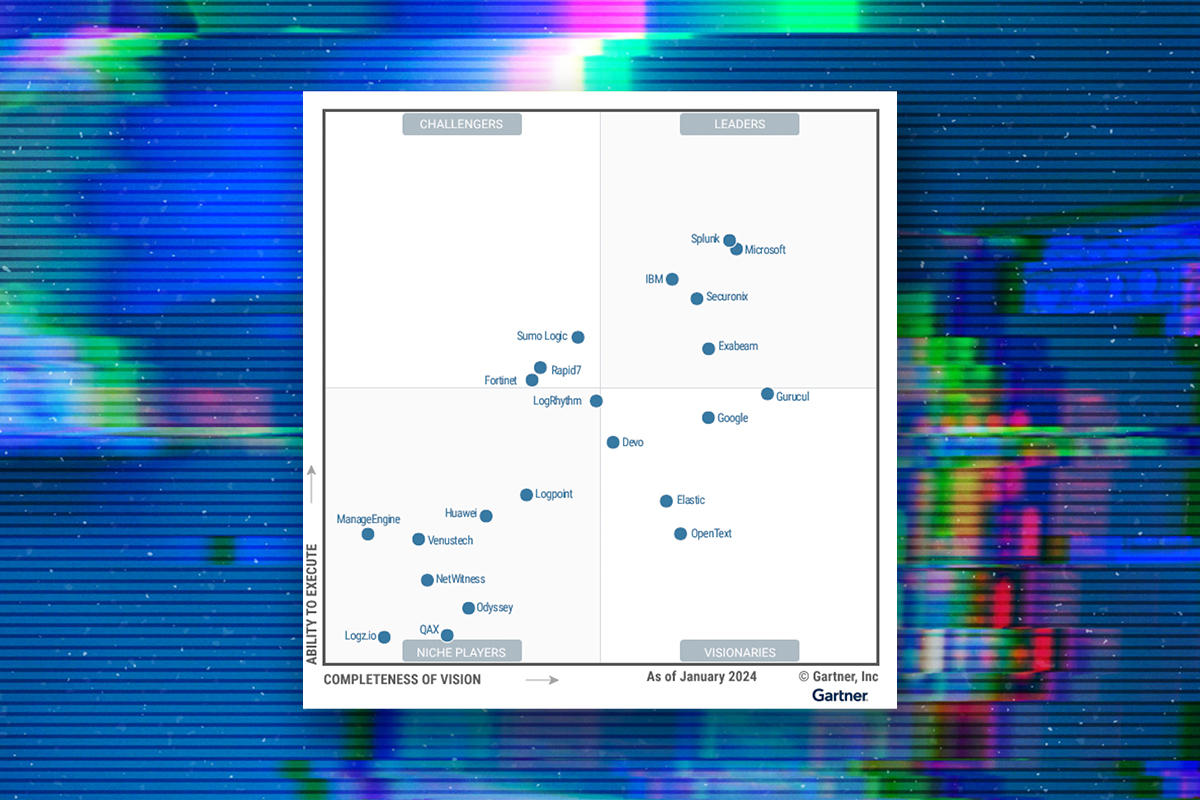
2024 Gartner Magic Quadrant for SIEM
Devo was recognized as a Visionary in the Gartner® Magic Quadrant™ for SIEM based on our Ability to Execute and Completeness of Vision.
In a world where cyberattacks are becoming increasingly common, businesses need more robust processes and procedures at the organizational level. Both security systems and the teams that operate them should be regularly tested to assess their efficacy and response to an attack. This dual requirement has led to the development of the Red and Blue Team.
Inspired by their military ancestors, red and blue teams play a vital role in enterprise security. Blue teams identify enterprise vulnerabilities and assess the effectiveness of existing cybersecurity tools. Their counterparts, the red team, purposely attack the blue team’s defenses and attempt to penetrate IT systems. Simply put, red are the attackers, and blue are the defenders.
This article will explore the many aspects of red and blue teams: what they do, how they work, and how they work together. We will also mention the existence of purple teams and run through a quick case study to solidify your understanding.
For your reference, we have included a brief summarization of the main differences between the two teams. Further detail is provided later in the article.
| Red team | Blue team |
|---|---|
| Offensive mindset, focus on attacking the organization as a hacker might | Defensive mindset, focus on defending the organization |
| Carry out exercises for pen testing, social engineering, phishing, vulnerability exploitation, and physical security breaches | Carry out activities to implement IPS/IDS, detect and mitigate security threats, collect forensic data after a security incident, and develop security policies |
| Use pen testing frameworks, phishing frameworks, network scanners, and post-exploitation tools | Use network scanners, vulnerability assessment scanners, pen testing frameworks, intelligence, and forensics tools, and logging and analytics solutions |
| Report the organization’s security weaknesses to the blue team | Action the red team’s findings to strengthen enterprise cybersecurity |
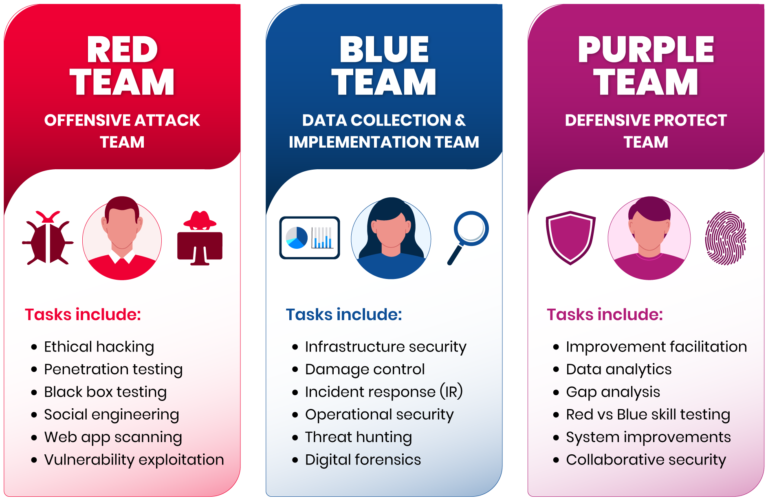
Comparison between red, blue, and purple teams (Source)
As discussed, red teams attempt to defeat corporate cybersecurity controls – as would a malicious hacker – to find cybersecurity weaknesses and implement fixes before real hackers can exploit them.
Once the team successfully breaks into a system, they try to understand where the company’s cyberdefenses are lacking and write up their findings in a post-attack report. The report describes the tools and techniques deployed, threat vectors, and recommendations to strengthen the company’s threat prevention, detection, and response capabilities. The blue teams can now better understand where existing defenses are weak and what countermeasures are required to prevent real cyberattackers. The red team’s “think like a hacker” approach enhances enterprise security and helps steer decision-making.
To make them more effective, Red teams conduct several types of security exercises, which include:
Red teams use several tools to break into enterprise networks, including:
Successful red team members should bring these skills to the table:
The blue team is the defender to the red team’s attacker. They analyze enterprise systems to identify weaknesses that real cyberattackers may exploit. They also implement the red team’s recommendations to patch systems, fix security-related configurations, and update security policies.
The blue team understands the company’s security weaknesses and uses this information to plan security improvements and protect the organization against threats. To conduct their exercises, they need data about current security gaps, which they acquire from the red team’s post-attack report. They may even perform penetration tasks to test the organization’s risk and threat exposure.
Blue teams are also responsible for security automation, threat intelligence gathering and analysis, incident tracking, and security information and event management (SIEM).
Blue teams will use monitoring tools to check for unusual or malicious activity on the enterprise network and conduct vulnerability scans, network traffic analyses, DNS audits, and DDoS testing.
The team also plays an essential role in guiding enterprise security investment and helps senior management decide which risks require what type of mitigating control.
Here are some examples of blue team tasks and responsibilities:
Blue teams also conduct or coordinate security training to improve organizational security awareness. However, the broad scope of their work has one overarching aim – to create a strong security posture. Every company needs a blue team backing up and augmenting their red.
Blue teams will use a wide selection of tools to carry out their day-to-day tasks:
Blue team members must have the following skills to function as effective security defenders:
Blue members must also have advanced knowledge of security detection tools and systems, including SIEM platforms, IDS, and IPS.
A purple team combines the best of red and blue. It is offensively and defensively focused and promotes collaboration and knowledge-sharing between red and blue members.
Red and blue teams bring different approaches and skill sets, which, when combined, help better secure the organization from existing and evolving threats.
Teams work best when communicating regularly and honestly, but this may not always happen. Any rivalry between teams can result in vital information and techniques being withheld from each other.
To remain effective, red teams must stay updated on new threats and share any relevant information with the blue team. Likewise, effective blue teams should constantly research new security techniques and share these with the red team.
Red teams should include detailed results in their post-test reports along with any recommended corrective measures. Similarly, blue teams should inform the red team if their monitoring tools detected the simulated attack. Red teams can subsequently adjust their attack techniques or look for other weaknesses to exploit.
When red and blue teams cooperate, they can form a collaborative security group stronger than the sum of its parts. Purple teams have diverse skills that enable them to function on either team and can perform regular spot checks when a full-scale red team/blue team exercise is not feasible or required.
Let’s run through a practical, albeit fictional, case study. ABC Inc. had recently been the target of a spate of cyberattacks within a short period. As part of their post-attack investigations, the security team realized that the organization’s security controls were inadequate and outdated. The company formed a blue and red team to address these gaps in its cybersecurity defenses.
The blue team first identified the company’s critical assets and conducted a risk assessment to determine each asset’s threat exposure and exploitable weaknesses. Next, they installed security software on all endpoints, implemented a SIEM platform to log and store network activity, and checked all firewalls, antivirus, and anti-malware configurations. They also analyzed all digital footprints to create a “baseline” of normal network activity.
The red team, which had no prior knowledge of the organization’s infrastructure, started their exercise by staking out and mapping the company’s entire environment, including its operating systems, open ports, and physical controls. They then harvested staff identities and launched phishing attacks to review if employees tended to enter their credentials into malicious websites when led to do so. They also used a password-cracking program to hack into sensitive corporate accounts and cloned an admin’s access card to gain physical entry to restricted areas.
The red and blue teams then pooled their findings, using their skills and experience to pinpoint the exact weaknesses in ABC Inc.’s security defenses. They also deliberated ways to prevent attackers from penetrating enterprise defenses, blocking similar attempts from real hackers.
Emulation exercises are the best way to build effective red and blue teams. These exercises leverage real-world tactics, techniques, and procedures (TTPs) to show the possible impact of a real-world attack. The two units can then work together to strengthen security controls.
It’s essential to develop solid rules of engagement (ROE) for both teams to govern the scope of their work. Each group could contain eight to fifteen members, but this number varies depending on the organization’s size, security goals, and skills.
Here are some more best practices that can help organizations make the most of their teams:
Unfortunately, security threats and cyberattacks are a fact of modern life that are with us for the long term. As a result, organizations need strong security defenses and the support of the good guys: red teams and blue teams. They may often appear to function on opposite sides but are, in reality, two sides of the same coin.
As we have seen, the red team has an offensive mindset and aims to break into enterprise systems, while the blue team is defensive and focuses on protecting the organization from threats and threat actors. These teams may use different methods and tools, but their goal is the same – to strengthen enterprise cybersecurity. Together, the red and blue teams bring together wisdom and skills that can enhance a company’s security posture and keep the bad guys out. There’s no question which team is “better” than the other because a practical and comprehensive security infrastructure needs both.