
SOAR Use Case: Triage Network Events
In the interconnected digital landscape, Distributed Denial of Service (DDoS) attacks pose a serious threat to organizations. These attacks overwhelm websites and networks with excessive traffic, disrupting normal operations, leading to financial losses, and damaging reputations. Over recent years, DDoS attacks have grown increasingly sophisticated, even affecting industry giants like Google, AWS, and Cloudflare. This guide explains how DDoS attacks work and provides actionable strategies for defending against them.
DDoS attacks originate from a botnet—a network of compromised internet-connected devices controlled by a single attacker. These devices, ranging from personal computers to IoT gadgets, are infected with malware. Once a botnet is formed, the attacker issues commands to flood the target with seemingly legitimate requests. This overloads the target, making it slow or entirely unresponsive to actual users.
DDoS attacks can take various forms:
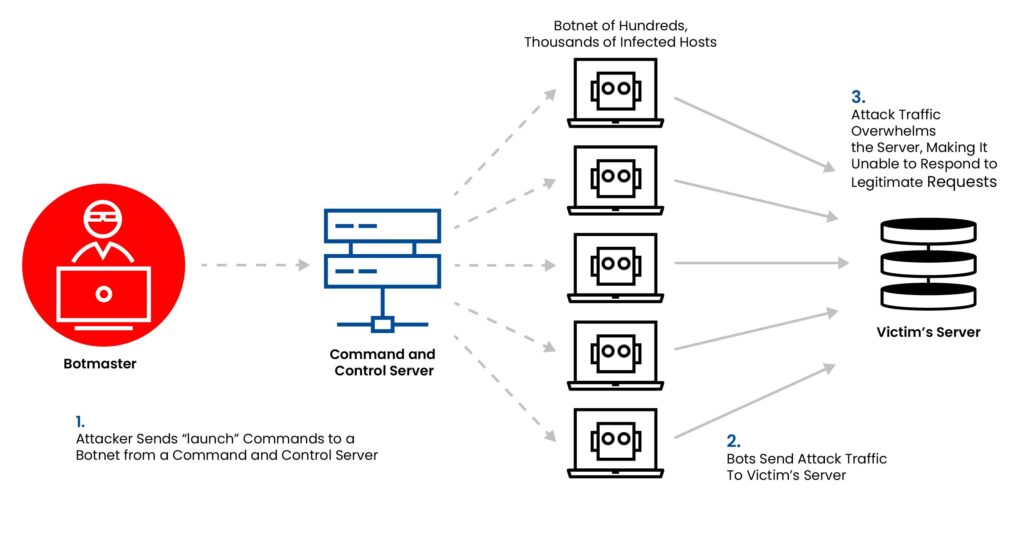
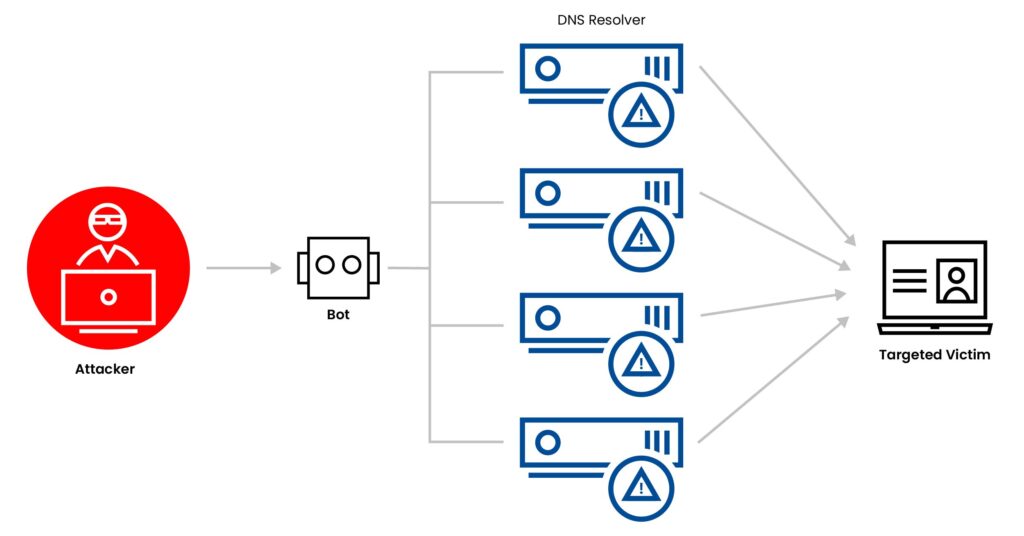
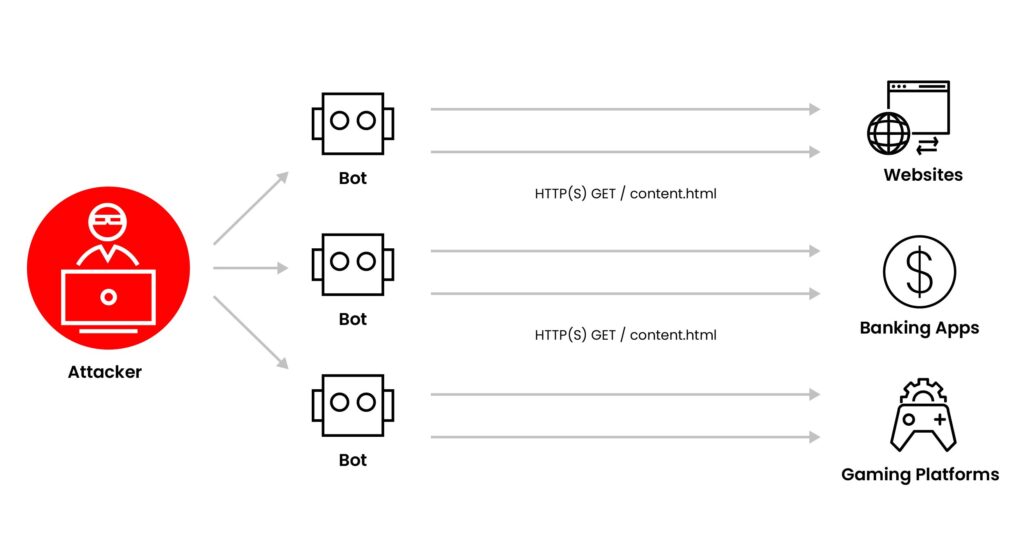
DDoS attacks frequently make headlines due to their widespread impact. A few notable examples include:
While DDoS attacks pose a significant threat, there are effective ways to protect against them:
When an attack does occur, organizations should have measures in place to minimize damage:
DDoS attacks continue to evolve, becoming more sophisticated and larger in scale each year. These attacks pose a growing threat to the digital world, but by understanding how they work and implementing proactive defense strategies, organizations and individuals can mitigate their impact. Vigilance, preparedness, and strong network defenses are key to safeguarding your online presence.