
Is Your Supply Chain Partner Your Biggest Security Blind Spot?
A supply chain attack is a highly sophisticated form of cyberattack where malicious actors compromise a service provider or vendor to gain unauthorized access to its clients or end users. These attacks target vulnerabilities within the software supply chain, which is often the weakest link in an organization’s cybersecurity defenses. In recent years, supply chain attacks have surged by 2,600%, affecting organizations across industries. The infamous 2020 SolarWinds breach and the 2021 Log4j vulnerability have highlighted just how devastating these attacks can be, leading to massive financial losses, operational disruption, and reputational damage.
Supply chain attacks typically follow a multi-stage process:
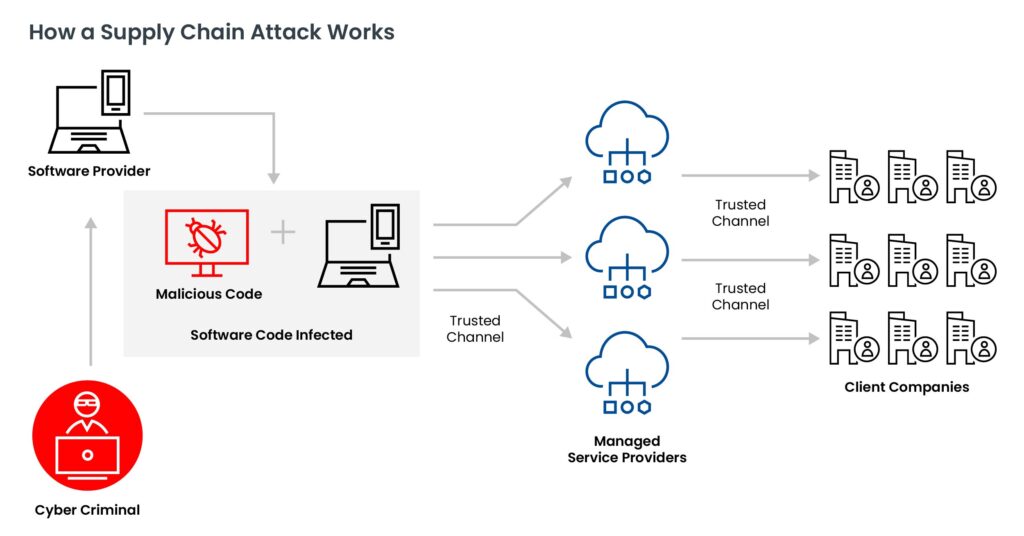
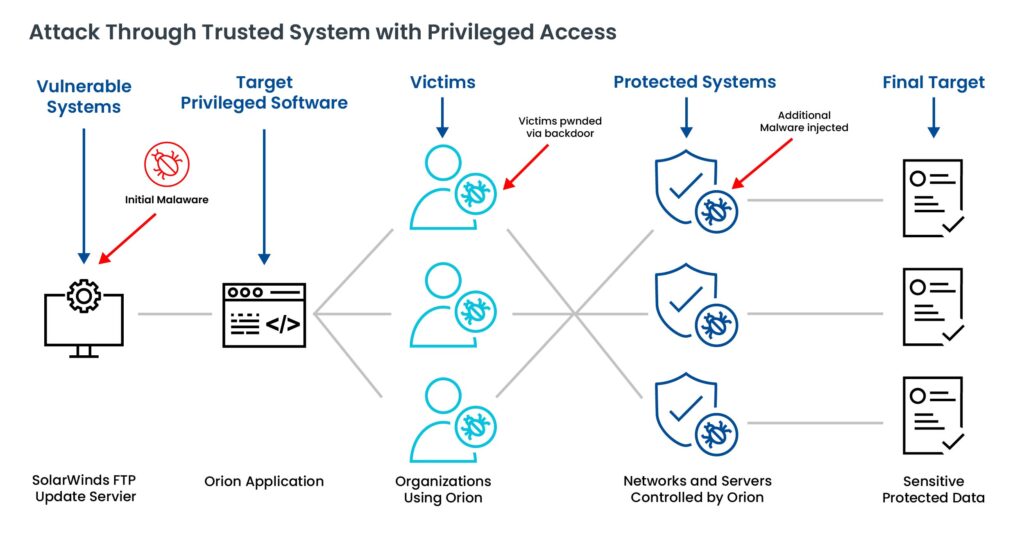
The consequences of a supply chain attack can be far-reaching, affecting not just the targeted organization but also its customers and partners:
While supply chain attacks can be challenging to detect and prevent, implementing the following best practices can significantly reduce risk:
The threat of supply chain attacks is more significant than ever as businesses increasingly rely on digital tools and third-party vendors to conduct daily operations. To minimize the risk:
By staying informed and adopting proactive security measures, organizations can significantly reduce the likelihood of falling victim to supply chain attacks.