
SOAR Use Case: Malicious PowerShell Commands
Ransomware is a type of malicious software that encrypts files or locks users out of their systems, demanding payment to restore access. These attacks can cause severe disruptions to operations, expose sensitive data, and lead to substantial financial losses for both individuals and organizations. According to the Verizon 2024 Data Breach Investigations Report, ransomware accounts for approximately one-third of all cyberattacks, making it one of the most prevalent and dangerous threats today.
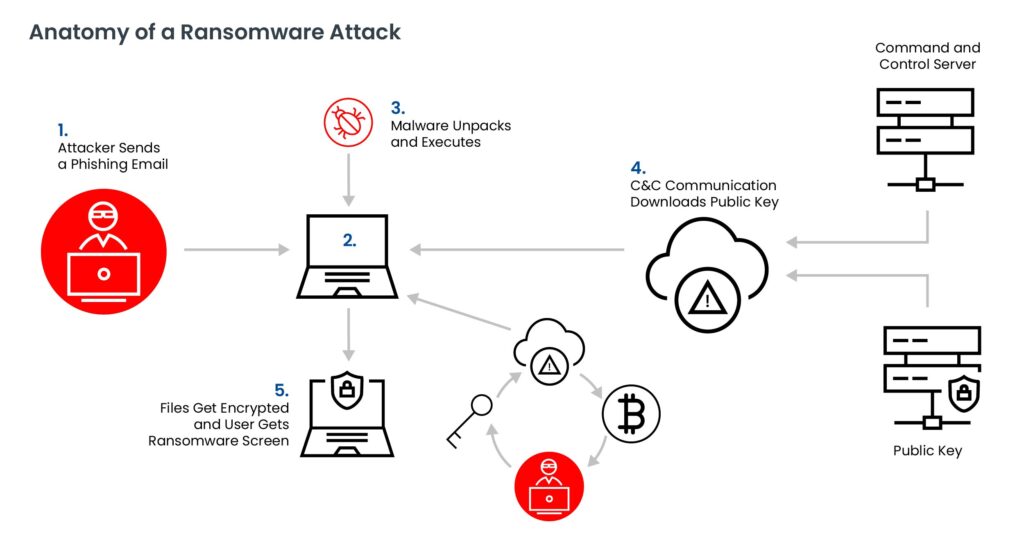
A typical ransomware attack follows these stages:
Ransomware comes in various forms, each with unique characteristics designed to extort victims:
Ransomware attacks are not just theoretical; they cause real-world damage to businesses and individuals:
The repercussions of a ransomware attack can be devastating:
Proactive measures are essential to mitigate the risk of ransomware attacks. Some best practices include:
Ransomware is an ever-evolving threat that requires businesses and individuals to stay vigilant. With regular backups, comprehensive security monitoring, and employee training, organizations can minimize the risk of a ransomware attack. Business leaders and IT professionals must adopt a multi-layered defense strategy to protect their data and avoid falling victim to these costly attacks.