
Our SOC Performance Report found that it takes an average of seven months to fill open SOC positions, and 55% of those doing the hiring are struggling to find qualified staff. As a result, SOC resources are strained, putting the team at risk for fatigue and burnout, which can cause them to miss critical alerts. Research has shown this is a widespread issue, too, as most SOCs waste an average of 10,000 hours annually validating unreliable and incorrect alerts.
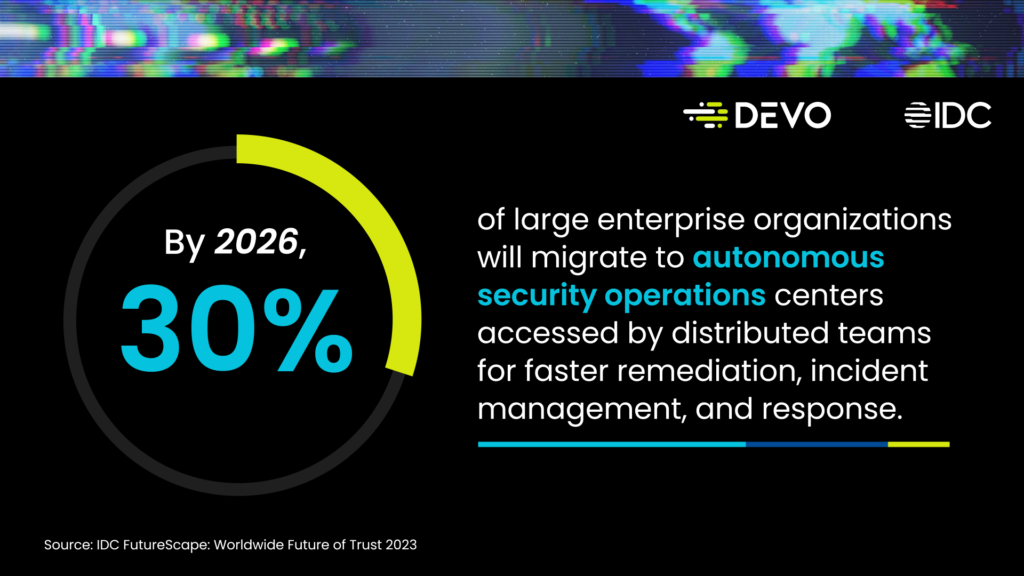
The inefficiencies happening in the SOC are also being scrutinized by the C-suite. According to the IDC FutureScape: Worldwide Future of Trust 2023 Predictions, 45% of CEOs, fatigued by security spending without predictable ROI, will demand security metrics and results measurement to validate investments in their security programs by 2025. Therefore, CISOs and cybersecurity leaders must ensure their teams deliver and demonstrate their value.
How Automation Fits In
Historically, it’s been up to analysts to sift through alerts, classify, and determine which ones require further action. This work is both monotonous and stress-inducing. Businesses must take proactive steps to augment their teams with automation to free them from the shackles of overloaded workloads, alert fatigue, and burnout. That’s where an autonomous SOC comes in, but it can be quite a big step on the SOC maturity curve for many organizations.
To begin the journey to an autonomous SOC, organizations should invest in next-gen SIEMs and security analytics platforms that have a multi-year roadmap that will enable them to:
- Quickly ingest data in a scalable fashion while accessing powerful analytics to derive insights from that data;
- Perform autonomous alert triage and threat hunting with attack-tracing AI;
- Automatically create playbooks to make it easier to track, collaborate, respond, and report on security incidents;
- Tap expertly-curated and community-sourced security content to fill the knowledge gaps of in-house SOC teams.
Cybersecurity leaders must carefully evaluate vendors to determine whether they can offer these capabilities in a cost-effective manner.
Economic Considerations
The pricing model of the Devo Platform is simple — organizations only pay for data ingested, averaged over 30 days. The price includes support, SIEM, SecOps, ITOps, machine learning, and automation functionality. We include 400 days of hot storage in the default license cost — which is the most of any vendor in the space.
Our benchmarks show that organizations can ingest 10x the amount of data, at 10x the speed, and at half of the total cost of ownership (TCO). How? Devo’s proprietary architecture reduces infrastructure overhead compared to traditional platforms. These savings are passed over to you with lower subscriptions, higher data retention, and free premium applications so you can scale, eliminate data blind spots, increase alert fidelity, improve performance, and accelerate MTTR.
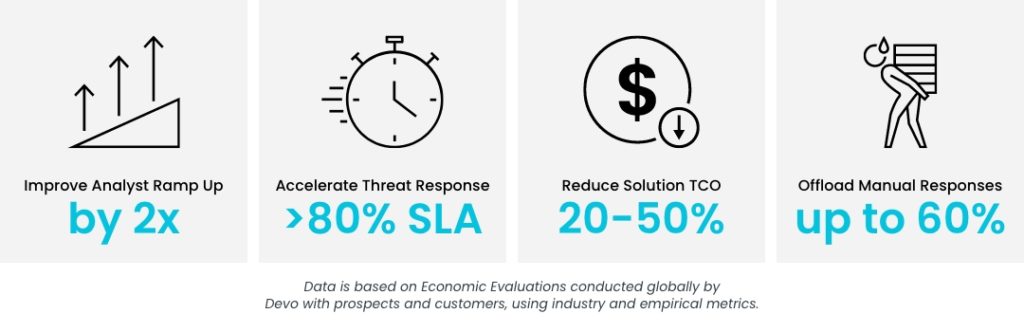
Devo can help you rightsize your security budget and modernize your SOC. We work with you to ensure a fluid and seamless transition from legacy solutions, as our team is extremely well-versed in a variety of migration types. And our customers agree the move is worth it, with one SOC manager saying, “Every individual I have worked with at Devo has gone above and beyond to jump in and assist from presales to engineering support.”
How to Get Started
Are you curious how the Devo Platform can help you? Take a self-guided tour of our Intelligent SIEM to get an idea of how our platform works.
After you have seen the platform yourself, you can request a call with our team to take a deeper dive with a formal evaluation. We’ll review your current SIEM and SOAR solutions, assess your current goals and challenges, prescribe use cases, and find ways to reduce your TCO while helping your organization realize more benefits from its security stack.




