
SOAR Use Case: Phishing Triage
Phishing attacks are deceptive attempts by cybercriminals to trick individuals into revealing sensitive information or downloading malicious software. According to CISA, phishing typically involves harmful links, emails, or attachments designed to appear as though they are from a reputable source. Attackers often impersonate trusted individuals or organizations through email, text messages, direct messages, or even phone calls to manipulate their targets. The growing sophistication of phishing campaigns, particularly with the help of AI, makes them increasingly harder to detect.
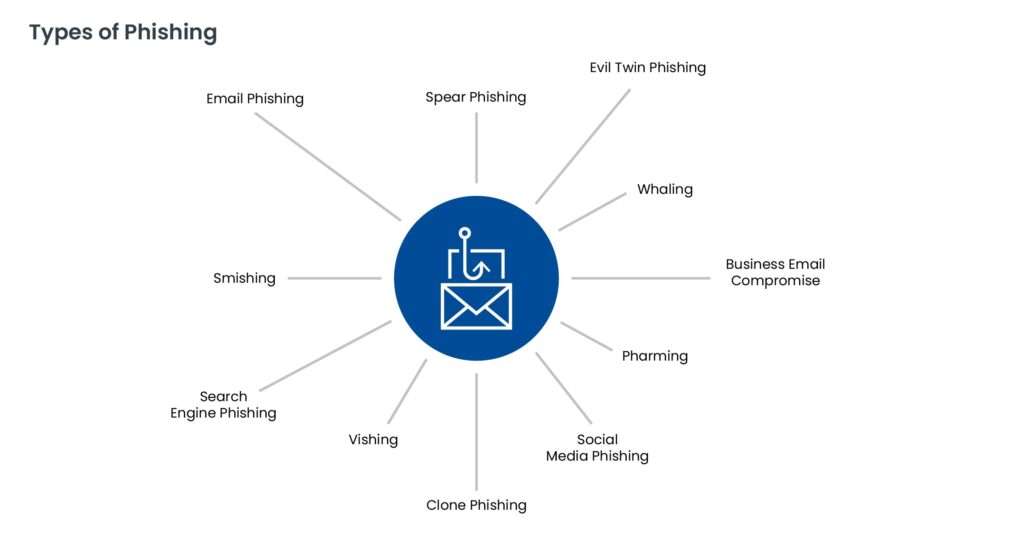
The phishing process typically follows these steps:

Phishing attacks frequently make headlines due to their effectiveness and scale. Some recent examples include:
Phishing attacks can lead to serious consequences, including:
To safeguard against phishing, organizations should implement several proactive measures:
Employee awareness is critical to defending against phishing. Regular training sessions should include common phishing red flags, such as:
Unusual Email Domains: Always check the email domain for legitimacy. Phishing emails often use domains that look similar to legitimate ones but contain slight misspellings or extra characters, like “amaz0n.com” instead of “amazon.com.”
Phishing attacks are becoming more sophisticated, but with the right precautions and awareness, organizations can mitigate their risks. Employees are often the first line of defense, and a well-informed team can prevent many phishing attempts from succeeding.