Devo Behavior Analytics
UEBA, or User and Entity Behavior Analytics, is a cybersecurity solution that uses machine learning and advanced analytics to detect anomalous behavior by users, devices, and other entities within an organization’s network.
Unlike traditional security tools, which focus on known threats, UEBA identifies patterns and deviations from normal activity, enabling proactive threat detection and reducing false positives.
Devo Behavior Analytics can help uncover anomalous user and entity behavior throughout your organization, delivering next-level risk context across the entire MITRE ATT&CK framework and rapid time to value.
UEBA collects logs and data from sources like user activity, network traffic, and system events. Using machine learning, it creates behavior profiles for each user or entity and continuously monitors them. If a user or entity exhibits unusual activity—such as logging in from an unfamiliar location or accessing high-risk files without previous history—UEBA flags this behavior for further investigation. Security teams can then review and respond to high-risk anomalies as needed.
UEBA and SIEM platforms are individually powerful tools, but their integration creates a more robust, proactive security ecosystem. Here’s how they complement each other:
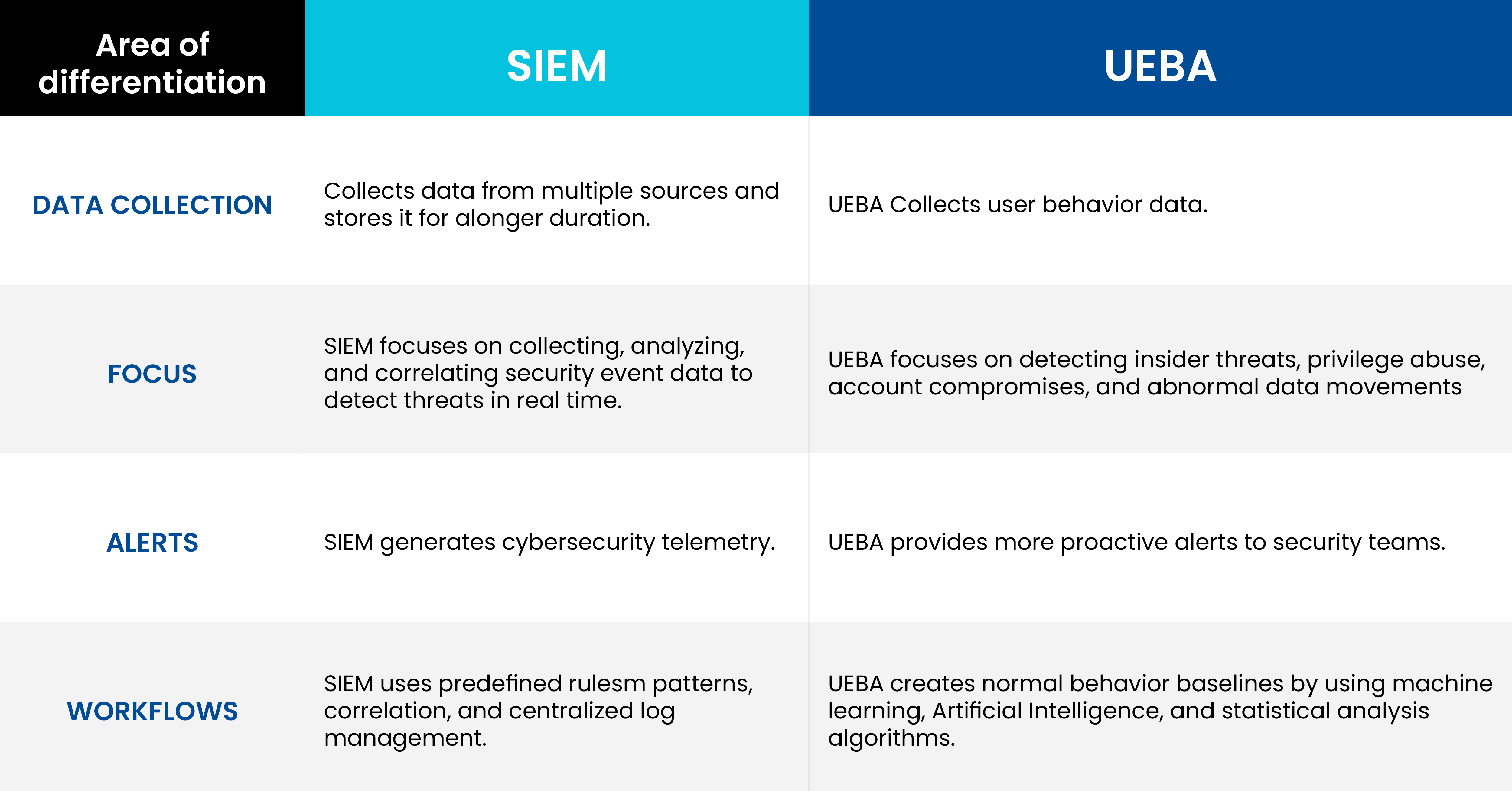
By integrating UEBA and SIEM, organizations gain a comprehensive approach to detecting, analyzing, and responding to threats. While UEBA focuses on behavioral anomalies, SIEM adds contextual depth and correlation, enabling faster and more accurate incident response. Together, they provide a security strategy that is proactive, adaptive, and resilient.
As UEBA evolves, expect further integration with AI to enhance predictive analysis, providing earlier detection of emerging threats. UEBA is merging with other security solutions, such as SIEM and SOAR, to create unified detection and response platforms. This evolution aims to streamline threat detection processes, improving response time and detection accuracy across complex environments.