
As revealed in the 2021 Devo SOC Performance ReportTM — which is based on the results of a survey of more than 1,000 security practitioners — organizations are frustrated with their SOC’s lack of effectiveness in performing its vital work. To combat the concerns the survey identified, it’s important for SOCs to refine how they operate.
This includes the role security automation technologies can play in improving SOC performance and alleviating analyst stress caused by overwork and performing repetitive, mind-numbing tasks, which can lead to analyst burnout. In fact, according to the report, 63% of survey respondents said that on-the-job pain in the SOC has caused them to consider changing careers or leaving their jobs.
Here are three of the most valuable SOC use cases to help reduce analyst burnout:
- Detect previously seen “known threats” without analyst intervention
- Validate the severity of threats for proper prioritization and resolution
- Augment Tier-1 analysts to improve team retention and effectiveness
In this fourth post in our blog series revisiting key findings of the 2021 SOC Performance Report we’ll dive into each of these use cases and the challenges they address.
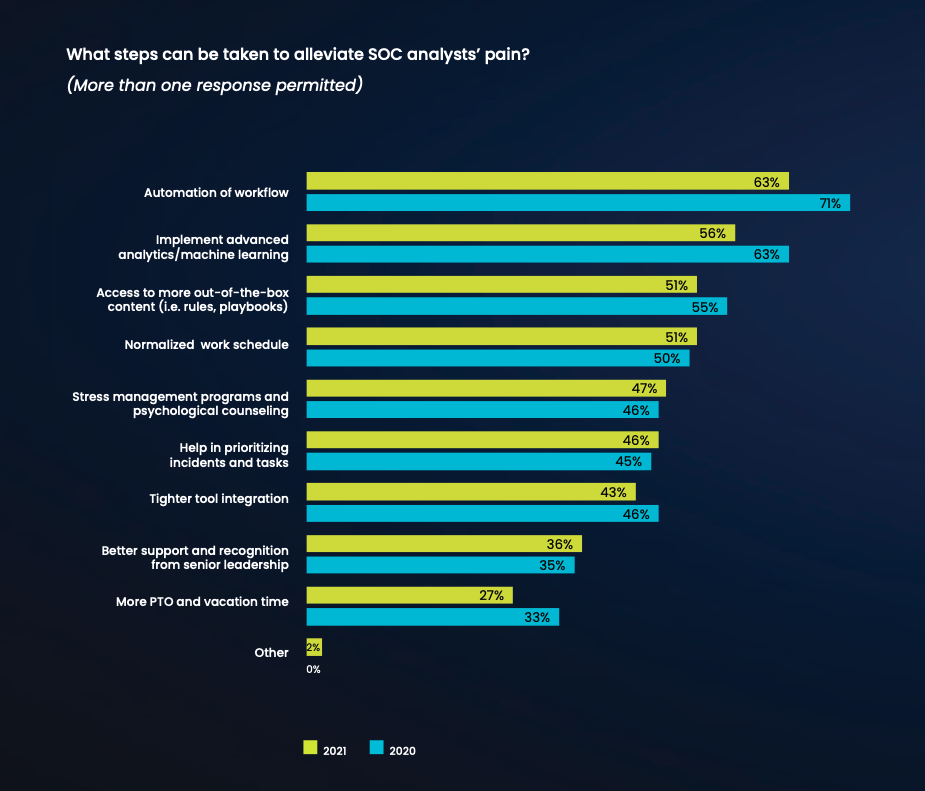
What Can Be Done to Rein in the Pain?
With such high numbers of SOC workers identifying job pain as possibly driving them to quit their jobs or choose a new career, there is no shortage of ideas for what organizations can do to try and at least minimize the pain afflicting analysts. In 2021, workflow automation was the top choice for how to alleviate the pain of SOC work, although fewer respondents chose it this year than in 2020. Another technological approach — implementing advanced analytics/machine learning — was the second most popular response.
Use case #1: Detect already-known threats — without analyst intervention
The key to successfully deploying automation as part of a next-gen security information and event management (SIEM) solution is identifying the areas of SOC analyst workflow where automation can be most effective. One of the best use cases for automation in the SOC is detecting known threats —malicious code that has been seen previously. Security teams can build playbooks to effectively automate the mundane steps related to detecting those known threats. This gives analysts, especially well-paid senior analysts, more time to focus on higher-level, critical tasks.
Use case #2: Validate the severity of threats for proper prioritization
Threat actors use automation to deploy constantly changing advanced persistent threats (APT) in their unending effort to breach enterprise security. They automatically execute a flood of attacks and diversions that can overwhelm even the best human analysts. It’s time for SOCs to use automation to thwart these efforts and level the playing field.
Every SOC typically has an explicit incident-handling procedure in place, defining processes, procedures, and technologies. When analysts see threat activity, the SOC automation playbook goes into action to validate how serious a threat is and any damage it may have caused. Without an automation playbook, analysts would have to do a tremendous amount of manual work, such as searching firewall logs to see if all malicious activity was successfully blocked. This would give adversaries more time to accomplish their missions. Automation is a big step toward eliminating that advantage.
Use case #3: Augment and power up your Tier-1 analysts
When security analysts hear the word automation, they may jump to the conclusion that it means they will be replaced by machine learning and artificial intelligence technologies. However, automation can actually augment analysts, particularly the Tier-1s who spend a lot of time glued to screens searching for threats and hoping they don’t miss anything that could cause a major problem.
Automation makes the SOC operate more effectively and efficiently, while freeing analysts from routine, boring tasks no one wants to do and which contribute to unacceptably high levels of burnout. Automating those mundane tasks enables analysts to do what they do best—focus on the threats that really matter to their organization.
Automation also can enhance junior analysts’ career development. Automating routine tasks gives Tier-1 analysts more time for training and development. It enables them to collaborate with experienced colleagues on the critical work of identifying and stopping the most dangerous threats. Organizations get a team of better trained, more experienced analysts who have greater job satisfaction. This means they are more likely to stay with the organization long term because they know they are making a meaningful contribution to its success.
There are many other valuable insights to be gleaned from this survey of professionals who must deal with the challenges posed by today’s state of the SOC. Next up in our blog series: How to Foster a Good SOC Culture.
Read the full 2021 Devo SOC Performance Report to learn more.



