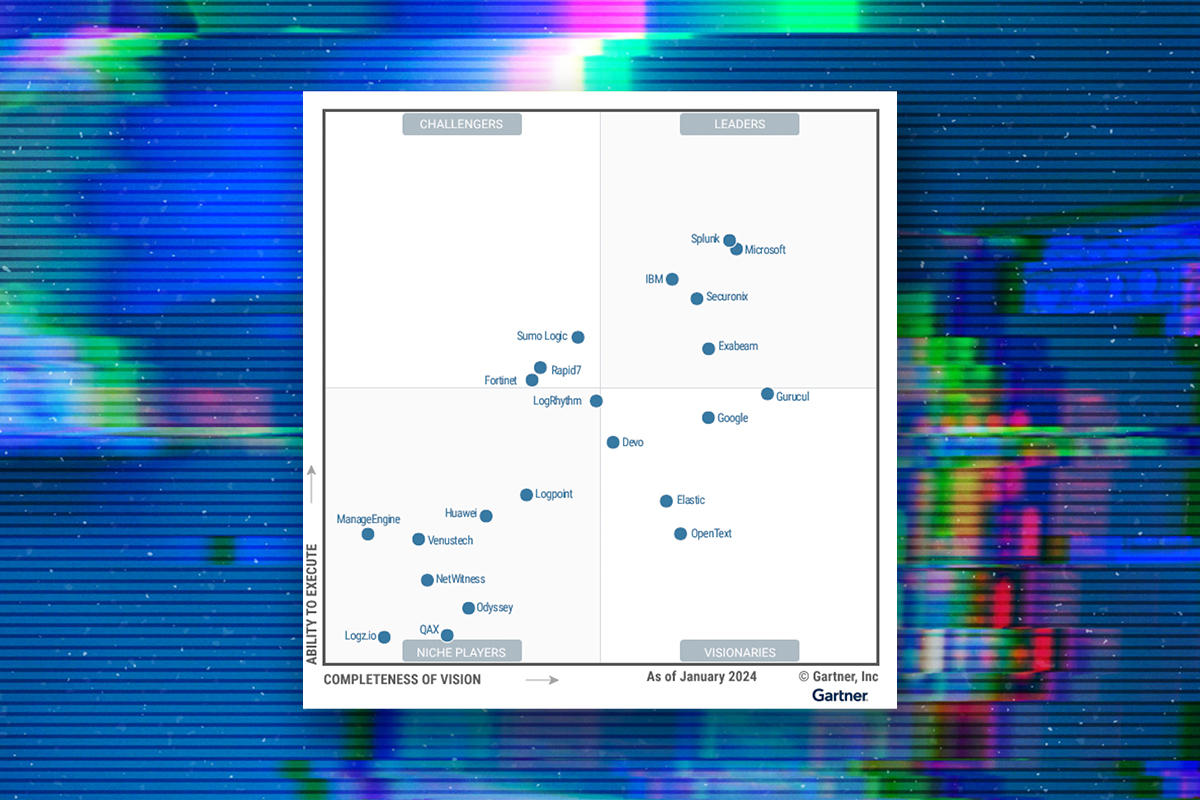
2024 Gartner Magic Quadrant for SIEM
Devo was recognized as a Visionary in the Gartner® Magic Quadrant™ for SIEM based on our Ability to Execute and Completeness of Vision.
As the cyberthreat landscape expands, it’s no longer a question of if your organization will be attacked, but when. To ensure that you’re not caught unawares, you must prepare for such incidents with a comprehensive Incident Response (IR) plan.
An IR plan can help you contain the impact of a security incident, minimize damage, and prevent others from recurring. However, to create one, you must first understand the Incident Response life cycle.
This article explains the various steps of the NIST incident response life cycle, their importance, and some best practices to optimize IR for your organization.
| What is the IR process? | The process of preparing for, detecting, mitigating, and preventing cyber threats and data threats |
| What is an IR plan? | A comprehensive document that details how an organization will detect and respond to cybersecurity incidents, and prevent recurrence |
| What is the IR life cycle? | A series of steps that enable enterprises to anticipate, detect, remediate and contain security events |
| IR life cycle frameworks | Popular frameworks are: NIST, SANS, and ISO |
| NIST IR life cycle | Consists of 4 phases:PreparationDetection and AnalysisContainment, Eradication, and RecoveryPost-incident activity |
Incident Response (IR) refers to a plan that documents how an organization should respond to a cybersecurity incident to contain it and minimize damage. It also provides a systematic, methodical and proactive approach to:
The IR life cycle consists of a series of steps that can help your organization implement effective strategies to anticipate, remediate and contain a security event. It emphasizes anticipation, preparation and speed so you can respond quickly to incidents and minimize their damaging effects.
As the name suggests, the IR life cycle is a cycle and not a linear activity. This is because its phases do not work in isolation, but impact and affect one other. For example, in the NIST’s IR lifecycle, the “Post-incident activity” phase provides critical inputs for the “Preparation” phase. Similarly, the findings from the “Containment, Eradication and Recovery” phase inform and help improve the “Detection and Analysis” phase.
Such interconnections also enable cybersecurity teams to:
As an added benefit, the IR lifecycle process enhances the response abilities of each team member and can lead to greater job satisfaction.
The NIST IR life cycle consists of 4 stages:
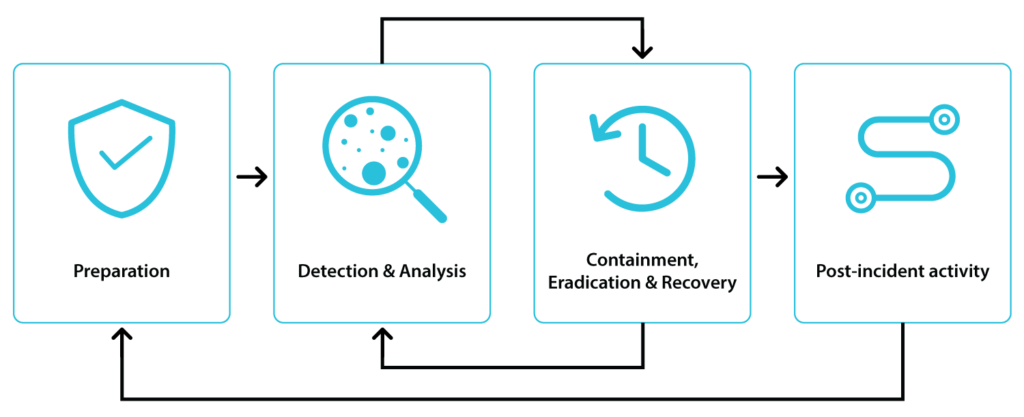
NIST Incident Response Lifecycle stages (source)
These phases are explored in more detail in the coming sections.
Aside from NIST, three other popular IR frameworks and their phases are:
| SANS | ISO/IEC 27035-1:2016 | SecureWorks | ISACA | NIST phase equivalent |
|---|---|---|---|---|
| Preparation | Plan and Prepare | Prepare | Planning and Preparation | Preparation |
| Identification | Detection and Reporting | Detection & Analysis | Detection, Triage, and Investigation | Detection and Analysis |
| Containment | Assessment and Decision | Containment & Eradication | Containment, Analysis, Tracking, and Recovery | Containment, Eradication and Recovery |
| Eradication Recovery | Responses | |||
| Lessons Learned | Lessons Learned | Post Incident Activity | Post-incident Assessment Incident Closure | Post-incident activity |
These frameworks use different verbiage for their phases, but regardless, the purpose of every framework is to provide a systematic methodology to prepare for cyber incidents, mitigate their impact, and improve incident response abilities. It is also worth noting that no one framework is “better” than another. You can choose any framework and customize it to your organization’s structure, operational requirements, strategic goals, and specific IR needs.
The four phases of the NIST IR life cycle are all crucial for effective ongoing incident response. These phases are:
When a security incident occurs, you need to be prepared to quickly assess the threat, predict its potential impact, and mitigate any damage. The threat may come from an external source such as a cyberattacker armed with malware, or an insider threat caused by a careless or malicious employee. It may also be a physical type threat to your assets. A lack of preparation can lead to serious financial, compliance and reputational repercussions that can affect your organization and its brand for a very long time.
In this initial phase, your IR team focuses on incident prevention. They will also implement strategies to protect the organization by carrying out some or all of the below activities:
| Activity | Purpose |
|---|---|
| Compile an asset inventory | Identify assets that may be the target of a data breach |
| Rank assets by level of importance | Implement protection strategies based on the business criticality of assets |
| Monitor asset traffic patterns | Create baselines to detect anomalous or suspicious behaviors |
| Conduct regular risk assessments | Identify risks, threats, and exposures, and their likelihood and potential impact |
| Vulnerability management | Regularly identify, assess, report on, prioritize, manage, and remediate security vulnerabilities |
| Set up a “war room” and other IR tools | Set up a centralized and shared command center – either a physical location with supporting infrastructure or a cloud-based app – to aggregate the information required to provide a comprehensive view of incident details and speed up decision-making during incident response |
| Create a communication plan | Specify who to contact, how, and when in case of an incident |
| Design an employee training and awareness plan | Clarify roles and responsibilities in case of a security incidentEnsure that everyone understands the IR process |
| Develop IR drill scenarios | Evaluate the IR plan, and its strengths and weaknesses |
| Get IR funding | Get funding and approval for the IR program |
| Implement IR controls | Strengthen incident detection, response, and remediation to secure the organization, and protect its IP assets and brand value |
At the end of this process, the team will be able to create a clear IR plan to categorize, prioritize, and respond to a security incident. They will also integrate this plan with other organizational plans (e.g. Disaster Management, Data Recovery, etc.) to ensure that all security incidents are handled properly at the enterprise level, without impacting business continuity.
This is a crucial phase because this is where the IR team starts analyzing an incident. They determine its prioritization, notify relevant stakeholders, and start putting together required documentation. It’s essential to define the standard operating processes, steps, and action items during the preparation phase. If new processes are identified, they should be clearly documented to improve future IR efforts. This flexibility to add new processes makes the IR life cycle a cycle rather than a linear series of steps.
To analyze the incident, the IR team will try to determine its entry point, breadth, and symptoms. To do this, they will ask questions like:
This detailed analysis will inform their response and remediation strategies.
The aim of containment is to prevent a security threat from spreading. To do this, IR teams may:
They may also perform forensic analysis to get deeper insights into the event. They will gather, review and examine evidence to understand how the incident occurred, what its scope was, which assets were impacted, and how a recurrence can be prevented. They will also preserve the evidence in a manner consistent with established best practices to ensure that it can be admissible later in a court of law if necessary.
Eradication means removing the threat. This is essential if the threat has already entered the enterprise environment and may spread further to cause more damage. Eradication ensures that the IR team can prevent this damage.
Recovery aims to recover data and get all affected systems back to business after an incident.
This last crucial phase enables IR teams to learn from their experiences following a security incident. They look for its root cause and assess ways to prevent any further recurrence.
In addition, they assess existing IR procedures to determine what worked well and what didn’t. Such ongoing assessments and a focus on continuous process improvement reveals gaps, and show where improvements are required to strengthen enterprise security defenses.
Suppose your organization is hit by a ransomware attack. According to the NIST IR life cycle, IR doesn’t start when the attack actually happens; it starts before, during the Preparation phase.
Preparation: The IR team develops the processes for the incident, ensuring a quick and efficient response should an attack occur.
Identification and Analysis: The team focuses on early identification of a possible attack as well as quick analysis to expedite containment, eradication, and recovery, thus minimizing the impact on the organization.
Detection: Following an attack, the team identifies the attack vectors, calculates risk, and implements detection measures for the identified attack vectors. They also implement prevention measures where applicable
Containment, Eradication, and Recovery: The IR team attempts to remove the ransomware, try to prevent its spread or lateral movement, isolate any systems that may be affected, and restore affected systems and data. They also try to prevent the beaconing of communication channels that may lead to malicious communication between the malware and the cyberattacker.
Post-Incident Activity: The team assesses the IR process to ascertain whether they could have done anything differently or better. For example, could stronger security controls, that may have prevented the attack, been installed? Could employees have been better trained, or prepared more thoroughly for such incidents? Also, are there any processes or policies that need to be implemented or updated to make future incident response more efficient, effective, and timely?
The threat landscape is constantly expanding and evolving. To keep up with new threats, it is vital to keep updating the IR plan. Also, make sure to incorporate any lessons learned after each security incident, thus improving the plan over time with hard earned experience.
Evaluate your IR program regularly, to gauge its effectiveness. To do this, you could implement the following testing strategies:
For effective IR, it’s important to establish clear workflows, communication plans, reporting procedures, escalation paths, and standard operating procedures (SOPs). These elements will help ensure that the process works smoothly and without costly mistakes. A clear and detailed plan will also help managers make informed decisions on security investments that strengthen cyber defenses.
It’s also important to regularly review IR processes and policies to find areas of improvement. Also assess systems and procedures (for example, those related to email communications, access controls, etc.) to ensure that there are no security gaps that may open up new attack vectors and make the organization vulnerable to attack.
Finally, don’t be tempted to skip the Preparation Phase. If bypassed, you risk continuously operating in a stressful cycle of firefighting and response. In such cases, the business concentrates on reacting to security incidents, rather than proactively improving their IR capabilities and security defenses.
Attackers are getting smarter and more sophisticated each day. To protect your enterprise assets and reputation, it is both insufficient and unwise to merely react as security incidents occur. Instead, you must implement proactive measures that prepare for IR scenarios in advance, thus ensuring successful containment and recovery. Here’s where the incident response life cycle can be a real value-add to your cybersecurity program. So, if you haven’t yet given thought to your organization’s IR plan, now is a great time to start.
Ideally, you should have a Security Incident Response Team (SIRT) that covers all aspects of security, including external threats, physical threats, and insider threats. They will ensure IP protection and mitigate other threats like active shooters. Many such teams use a Security Information and Event Management (SIEM) solution that consolidates log data, security alerts, and event information to help identify these threats, analyze them in real time, and mitigate their impact.