
The SANS 2023 Attack and Threat Report
Learn more about the current threat hunting landscape and discover ways to facilitate the critical work threat hunters are doing to protect enterprises.
Indicators of Attack (IoA) are forensic signs that typically surround a cyberattack – finding them warns that such an attack is likely to be in progress. Like Indicators of Compromise (IoCs), IoAs are also a threat detection strategy. Unlike IoCs, IoAs are proactive and work in real-time to detect an event before or while it happens.
While IoCs provide evidence of an attack and enable prompt response from security teams, IoC-based detection cannot detect sophisticated, new, or emerging threats. To identify and disrupt advanced attacks, you must collect, interpret, and contextualize many fragments of information early in the attack chain. It is also essential to understand the attacker’s intentions and techniques to keep them at bay.
Here is where IoAs come in.
Here are some solid examples of IoAs that you can use to prevent attacks and protect corporate assets.
| IoA | What it indicates |
|---|---|
| Public servers communicating with internal hosts | A data exfiltration attempt or command-and-control (C&C) server spreading malware |
| Persistent communication between internal hosts in a short period | Lateral movement or low and slow data exfiltration |
| Multiple honeytoken alerts from one host | An attacker has tried to exploit a resource (honeypot) |
| PowerShell.exe renamed | An attempt to make a malicious activity or malware download appear innocuous |
| Excessive SMTP traffic | An attempt to spread malware, capture sensitive information as part of a man-in-the-middle (MitM) attack, perform Distributed Denial-of-Service (DDoS) attack, or use a corporate server to send spam emails and perpetrate phishing scams |
An IoA is a “confirmed” event with a high probability of being an actual attack. IoAs function as an early-warning system that provides evidence of attacks before they increase in severity. They also help providea more contextual picture of the attack chain, so security teams can identify and contain potentially damaging events before they result in system compromise, network downtime, or data loss.
When analyzing IoAs, the specific exploit is of little concern. Instead, IoAs focus on detecting an attacker’s intent, actions, and methods. In short, IoAs look at an attacker’s tactics, techniques, and procedures (TTPs), not the threat or vulnerability type.
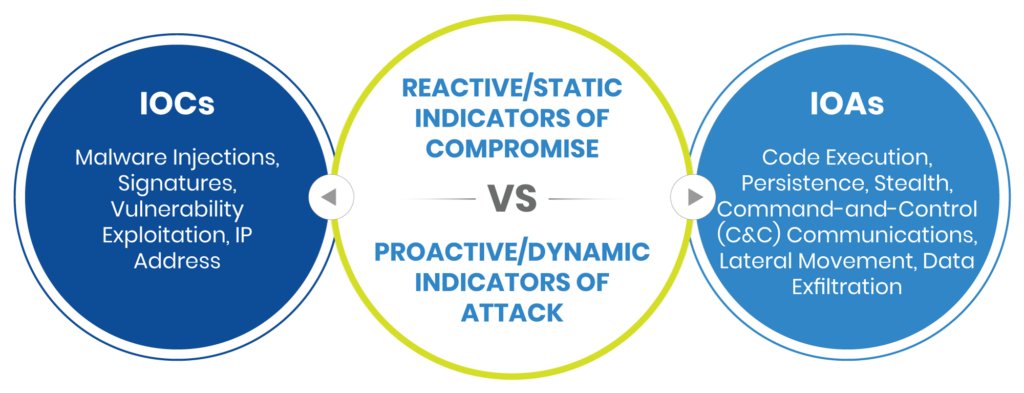
Image shows that IoCs are reactive where IoAs are proactive (Source)
An IoC provides signs of a cyberattack that has already occurred. In contrast, an IoA provides proactive and real-time evidence that an attack’s likely to occur or is currently happening. It thus enables security teams to stop an ongoing attack before it’s too late.
IoC-based threat detection methods are static because they focus on cyberattack footprints that remain unchanged over time. While threat intelligence enables organizations to defend against future attacks, they cannot stop attacks that are already happening. Conversely, IoAs can, which is why IoA-based detection is dynamic. IoAs also promote an understanding of attack lifecycle phases and an attacker’s techniques.
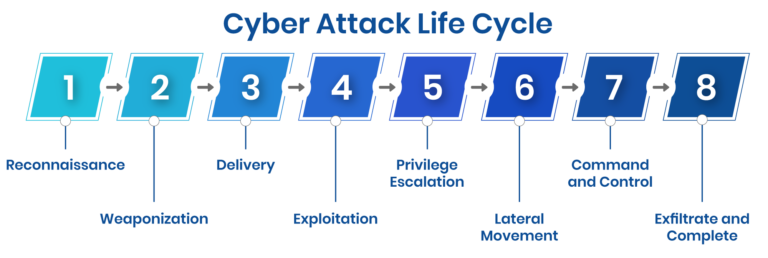
Cyber attack life cycle (Source)
Unlike IoCs, detected IoAs are not inherently harmful. Instead, they become “bad” based on the situational context and a threat actor’s intent. IoAs create a situational picture early in the attack lifecycle and provide greater visibility to fight off an attack before it can succeed. IoCs cannot do this.
Neither threat detection method is “better” than the other, though. Organizations need both to provide comprehensive threat detection and mitigation. IoCs aid attack investigation and help implement controls to prevent repeat attempts. However, only IoAs can detect active, in-progress attacks before the attacker can achieve their goal. They can also detect unknown threats like file-less malware, a capability that IoCs lack.
Here are five examples of IoAs that provide evidence of a likely cyberattack.
A public server communicating with internal hosts usually indicates a data exfiltration attempt. The external server may be a command-and-control (C&C) server that issues commands to a network of compromised hosts known as botnets.
The C&C server exploits these infected hosts to spread malware, extract data, or perform other damaging activities like Distributed Denial of Service (DDoS) attacks.
Once this IoA is detected, it’s crucial to quarantine any infected hosts. It’s also helpful to employ a Security Information and Event Management System (SIEM) to monitor network traffic and raise alerts about suspicious communications between external servers and internal hosts.
It’s also important to monitor:
Persistent but brief inter-host communications followed by malware reinfection within a few minutes of removal may indicate an Advanced Persistent Threat (APT). With an APT, an adversary gains initial access and moves laterally across the network, looking for high-value assets. To maintain ongoing access, they obtain increased privileges that allow them to move through other systems.
To avoid costly losses from APTs, you must find and remove the intruders early. An attacker’s dwell time can be reduced using an endpoint security solution. Tools with next-gen AV, behavioral analysis, prevention technology, and complete Endpoint Detection and Response (EDR) can automatically detect and respond to suspicious activity. Proactive threat hunting is also vital to find hidden threats and ensure that critical alerts are addressed on priority.
An activated honeytoken indicates that a cyber threat may be lurking near sensitive data or IT assets. These decoy resources appear legitimate to cyber-attackers, who are baited into exploitative actions, after which an alert is raised. Multiple alerts from the same host are an attack indicator that you should immediately investigate.
Honeypots enable you to uncover an attacker’s identity and strategy to help defend targeted resources. Honeytokens can also help build a more proactive cyber defense strategy for continued protection.
PowerShell is a legitimate shell framework for Windows systems that attackers leverage to create threats like file-less malware. They often rename the powershell.exe file to bypass security controls, hide their suspicious activities behind a legitimate process name, and ensure that any malicious activity or malware download appears innocuous.
So that threat actors cannot rename powershell.exe for malicious purposes, implement tools that can identify suspicious behaviors, and recognize the identity of all system utilities, including PowerShell. Further, native log sources, EDR, and other security tools can provide optics about processes, metadata, and files for greater visibility into renamed utilities.
Some attackers exploit the SMTP email protocol to send information to a C&C server. SMTP lacks authentication, which allows them to spoof genuine email addresses and launch phishing attacks. They can also access the SMTP server to spread malware, capture sensitive information as part of a man-in-the-middle (MitM) attack and launch DDoS attacks affecting network performance. Attackers may even use a corporate email server to send spam emails to perpetrate phishing scams.
Email protocols and frameworks like Sender Policy Framework (SPF), Domain Key Identified Mail (DKIM), and Domain-Based Message Authentication, Reporting, and Conformance (DMARC) can close SMTP gaps and prevent DDoS attacks and email spoofing.
Some other essential IoAs are:
When hunting for IoAs, EDR solutions should be deployed to detect any abnormal behavior on endpoints. You also should identify key performance indicators (KPIs), such as ideal/expected response times, to assess your security solutions’ detection and response capabilities. At the same time, explore attack mitigation strategies to ensure that each IoA is genuinely actionable and practical.
Further, you should augment a SIEM platform’s logging/alerting capabilities with advanced threat intelligence to correlate endpoint discoveries with network events to uncover additional IoAs. You should also review if any devices, systems, platforms, or configurations are more vulnerable to attacks than others and take corrective action.
A robust analytics architecture is helpful in aggregating information fragments to create contextualized intelligence for threat detection and remediation. Firewall, web server, and authentication logs should be fed into the SIEM and regularly analyzed to discover IoAs. These activities require human effort and can be time-consuming, so ensure that skilled people have sufficient time to conduct these analyses.
To fully protect your organization, IoC-based threat detection alone is insufficient. Instead, combine IoCs and IoAs to provide layers of defense that allow you to steer clear of sophisticated threat actors and emerging threats.
Indicators of Attack enable organizations to move away from traditional reactive investigation and recovery processes to proactive attack prevention. By hunting for IoAs, security teams can disrupt and block attackers before they can achieve their objective, whether moving laterally across the network, exfiltrating data, or launching a ransomware attack.