
The SANS 2023 Attack and Threat Report
Learn more about the current threat hunting landscape and discover ways to facilitate the critical work threat hunters are doing to protect enterprises.
As the cyberthreat landscape expands, organizations need better ways to proactively detect threats and defend their business-critical assets and data. That’s why they need Security, Orchestration, Automation and Remediation (SOAR) and Security Information and Event Management (SIEM) solutions.
While these cybersecurity tools share some common and complementary capabilities, they have different strengths, and so cannot be used interchangeably. To strengthen cybersecurity, organizations should understand these differences. Only then can they use these tools effectively to shore up their defenses.
This article aims to explore these differences in detail. For your convenience, we have included an executive summary that condenses these into the table below.
| SIEM | SOAR |
|---|---|
| Raises alerts; personnel must take action | Intakes alerts and automatically responds |
| Manual alert triage is required | Automated alert triage |
| Analytics engine must be manually tuned to differentiate between malicious and benign threats | Automatically differentiates between threats and acts accordingly |
| Attributed to alert fatigue among analysts | Orchestration and automation capabilities reduces alert fatigue |
| Basic data correlation capability and takes single decisions to trigger alerts (which may be false positives) | Dynamically pulls data based on decisions in playbooks or after asking for user inputs |
| Restricted to collecting log data from network, endpoint, cloud, and applications | Can also intake human inputs to make on-the-fly decisions to stop threats |
| Can only raise alerts; security personnel must still analyze each alert and decide on a course of action | Automatically responds to threats and takes appropriate action to protect the organization |
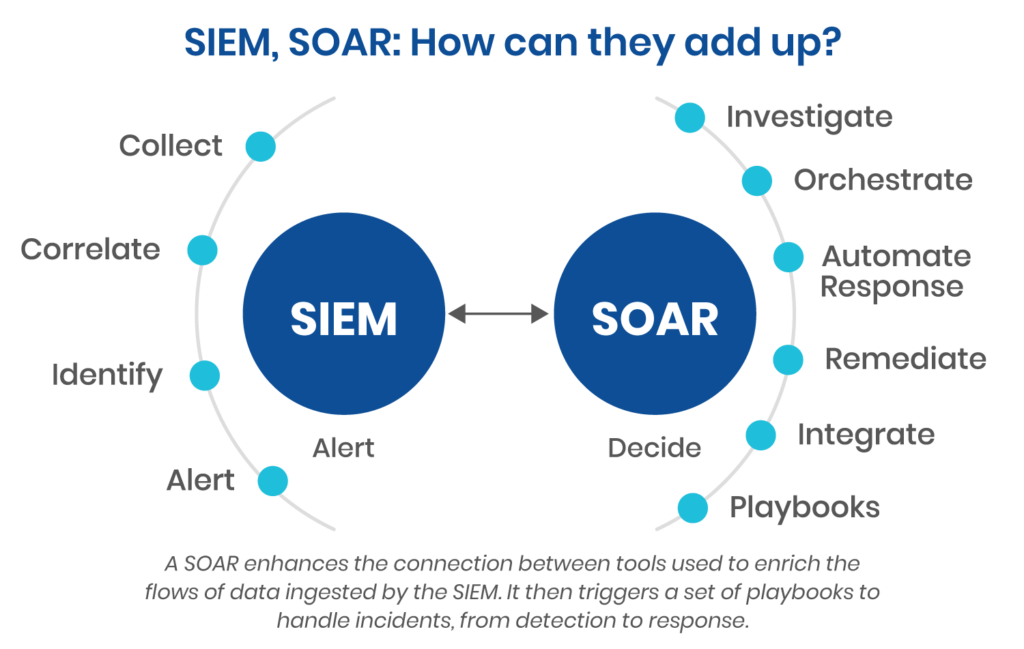
Image highlights the differences between SIEM and SOAR (source)
SIEM tools collect and aggregate log and event data from multiple sources including network devices, endpoint devices, cloud solutions, and business applications. They then analyze this data to pull actionable threat intelligence.
A SIEM platform raises alerts if it detects an anomalous activity or security issue. It also generates reports about security incidents and threats, then ranks them in order of criticality. Security teams can review these alerts and reports, taking action if needed, to protect the enterprise from adversaries.
The best SIEM platforms provide many benefits for security-conscious organizations, including:
SIEM tools correlate data from multiple sources and find patterns that may indicate the presence of a threat. Their reports and alerts enable security teams to quickly detect and respond to these threats.
Security administrators can view huge amounts of security data from one centralized location. Since they don’t have to hunt for intelligence in different places, they can quickly assess the threat and accelerate incident responses to mitigate any potential impact.
Many legal and industry regulations and frameworks around cybersecurity and data privacy require organizations to tighten their security perimeters, especially if they deal with sensitive personal, financial, or healthcare data. These include regulations like PCI-DSS, HIPAA, and SOC2 and frameworks like NIST Cybersecurity Framework (CSF). With SIEM, organizations can take advantage of aggregated, correlated data to understand and strengthen their security infrastructure based on compliance requirements.
Despite many benefits, a SIEM tool alone is not an effective bulwark against bad actors and security threats because it presents several shortcomings. These are explored below.
Security administrators must manually tune the analysis engine to ignore benign events and alert on malicious events. Only then can they continually differentiate between “anomalous” and “normal activity”. Consequently, they end up wasting precious time that could be better utilized in prioritizing and actioning incoming data.
The SIEM tool collects data from many sources so organizations can better understand their security landscape. However, this generates many alerts for security teams to analyze, prioritize, and remediate. This is often a difficult and time-consuming process.
Moreover, since teams have to manually investigate and validate each alert, it often results in “alert fatigue”. As a result, analysts may end up ignoring valid alerts, which makes the organization more vulnerable.
A Security Operations Center (SOC) consists of the tools and people that monitor the enterprise network, investigate security incidents, and act quickly to remediate threats. SIEM tools are most effective when used in formal SOC settings.
One reason for this is that SIEM platforms are data-hungry and generate huge volumes of alerts. Most systems don’t analyze alert behaviors, neither do they have the capability to separate real threats from false positives. In order to validate, process, and analyze these threats, human analysts are required.
Human input is also required to create the rules that govern SIEM data and raise alerts to suspicious behavior. Finally, since many alerts are generic, it can be difficult to correlate threats and determine what kind of action should be taken for a particular threat. Here again, the SOC team – or a managed SOC service – is required to ask the right questions and determine the appropriate responses.
SOAR tools are very similar in that they also collect, aggregate, and analyze security data from disparate sources, including SIEM. But they incorporate three crucial components not included in SIEM platforms:
Together, these capabilities provide an integrated cybersecurity solution for security operations automation of many of the initial processes involved in the incident response cycle. The extensive use of automation allows enterprises to respond to a significantly greater number of alerts while reducing analyst burnout.
Although SIEM and SOAR both aggregate security data, present alerts, and help with threat monitoring and response, there are several key differences:
SIEM tools mainly collect security logs from an organization’s network, endpoint, cloud, and applications. SOAR tools can collect data from all these sources, plus additional sources like endpoint security solutions, emails, threat intelligence feeds, cloud security and IoT device alerts, and vulnerability scan results.
In addition, SOAR platforms have the dynamic ability to pull data based on decisions in a playbook. This is something that SIEM tools cannot do. In addition, SOAR tools can interact with user inputs and make on-the-fly decisions to stop threats and protect the organization.
For instance, the tool can detect login attempts and automatically email the user associated with those login credentials to ask if they are trying to log into a particular system. If the user confirms that they are the ones trying to log in, the SOAR platform will stop the playbook and take no further action. But if the authorized user is not the one trying to log into the system, the platform will further analyze the login attempt and take appropriate action if it confirms that the account is compromised.
SIEM tools only raise alerts in the event of a threat or security incident. Human analysts must analyze these alerts and determine the investigation and remediation pathways. SOAR investigates alerts and automatically initiates remediation activity for more proactive cybersecurity.
SOAR solutions don’t require human inputs to set security rules. Plus, there’s no need to manually tune the analysis engine to teach the solution to differentiate between malicious and benign threats.
SOAR combines data collection, case management, alert generation and automated incident response into one integrated solution. It also addresses many of the limitations of SIEM. Here’s how:
With SOAR, all the security information required to detect, assess, and respond to incidents is easily available from one centralized interface. The tool also presents predefined workflows for incident response and reporting.
SOAR detects suspicious events, raises alerts, and automatically invokes investigation and remediation workflows. It can also independently respond to low-level security events to minimize the need for human intervention.
SOAR platforms help fine-tune alerts by correlating data from various systems and separating genuine threats from false positives. Since security personnel need to investigate fewer alerts, alert fatigue reduces and threat detection and response becomes more effective.
With AI and machine learning-led analyses, detection and response procedures are automated. Also, all threat intelligence and controls are available through a single pane of glass, thus reducing the time and effort required to assess, process, and action alerts.
SOAR platforms leverage playbooks to automatically respond to attack vectors and specific threats. The steps in a playbook can be fully automated or configured for one-click execution from within the platform.
Case management capabilities enable security teams to research, assess, and investigate threats from within a single case. They can also complete investigations faster via easily orchestrated tasks, such as opening tickets in a tracking system.
All in all, SOAR goes beyond SIEM’s capabilities to facilitate adaptive defense-in-depth that helps the organization improve its security posture.
The best way to understand how SOAR addresses the weaknesses of SIEM is with an example.
Suppose your SIEM platform detects what seems to be a “brute force” attack on your enterprise network and raises an alert. That’s it. At this point, your security team doesn’t know if a bad actor is trying to brute force passwords to break into an endpoint (true positive) or if a careless employee has simply mistyped their password multiple times (false positive). The team will have to manually investigate the alert to understand if there’s really a security breach. They will then take the appropriate action to contain the threat.
Here’s where SOAR steps in.
The SOAR platform will do more than simply detect the event. It will also investigate to understand whether it’s a real threat or a false positive. For example, it will compare the IP address of the person trying to log in against a list of suspicious/blacklisted IP addresses and domains. For this comparison, it will analyze and correlate the data acquired from various sources. If it determines that the detected IP address is malicious, it will automatically block it and prevent it from accessing the network.
Thus, when SOAR finds a real threat, it will analyze security data from multiple sources and automatically initiate threat remediation. Since threat analysis, investigation, and remediation will be done automatically and near-instantaneously, security staff won’t have to get involved. Plus, your organization can deal with the threat faster and more effectively than you could with a SIEM platform alone.
The right SIEM and SOAR tools can help you proactively detect threats, arrest attacks, and secure enterprise assets and data. For these reasons, it’s crucial to look for tools that include the following features and capabilities:
| SIEM | SOAR |
|---|---|
| data collection and aggregation from multiple sources | data collection and aggregation from multiple internal, external, and third-party sources |
| correlation of security incidents | correlation of security incidents |
| real-time threat and user activity monitoring | real-time threat and user activity monitoring |
| centralized logs | centralized logs |
| actionable threat intelligence and analytics | actionable threat intelligence and analytics |
| customizable and automated reporting | customizable and automated reporting |
| scalable | scalable |
| automation workflows for incident response | |
| case management | |
| ease of deployment with intuitive playbook builders and use cases for common security scenarios | |
| orchestration of incident response and management tasks |
Some popular open-source SIEM tools are:
Several open-source SOAR platforms are also available. These include:
In addition to the open-source tools mentioned above, many paid and commercial SIEM and SOAR platforms are also available. The choice would depend on an individual organization’s cybersecurity needs, goals, and budgets.
Further, as the SIEM and SOAR markets evolve, some platforms are emerging that
combine the capabilities of both tools. For example, Microsoft Sentinel (starting at $0) provides SIEM capabilities such as log management, real-time monitoring, and user activity monitoring, as well as orchestration and automated response. It therefore provides a single solution for threat visibility and hunting, attack detection and threat response. Enterprises with larger teams and a broader threat landscape may benefit from converged tools such as these, while smaller companies might be better off with separate SIEM and SOAR platforms.
We hope that this article provided a deeper insight into the key differences between SIEM and SOAR. SIEM tools continue to play a useful role in enterprise cybersecurity, albeit with a few weaknesses, which can otherwise be addressed by SOAR. This makes the two systems something of a dynamic-duo for your cybersecurity program. By implementing both SOAR and SIEM, organizations can achieve defense-in-depth, keeping the bad guys out of sensitive networks and data.