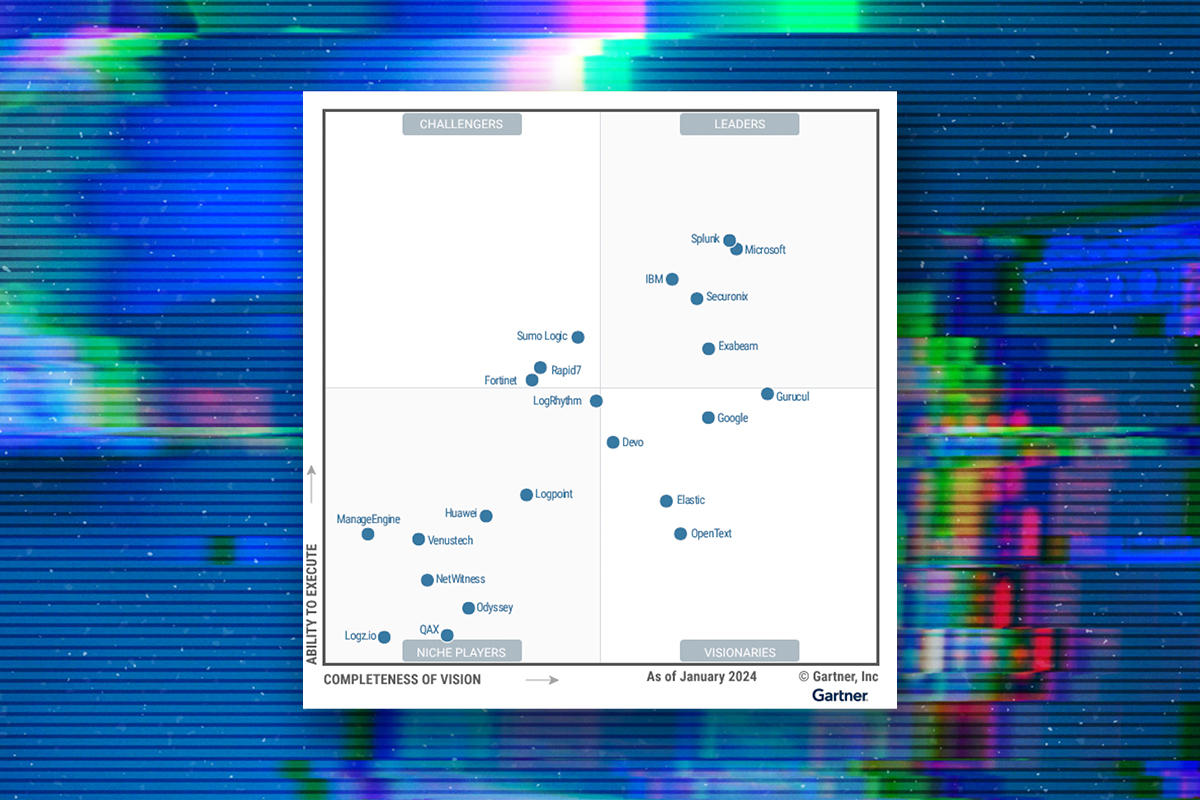
2024 Gartner Magic Quadrant for SIEM
Devo was recognized as a Visionary in the Gartner® Magic Quadrant™ for SIEM based on our Ability to Execute and Completeness of Vision.
The Security Operations Center or SOC is at the heart of many enterprise cybersecurity programs. A SOC enables organizations to manage their vulnerabilities, contain and eradicate threats, and streamline incident detection and response.
That being said, the SOC is not without its challenges. For one, disconnected security tools can increase operational overhead and decrease efficiency. Second, the shortage of skilled cybersecurity personnel makes it harder for firms to manage their threat landscape effectively. A third is that SOC team members may not be aware of the latest best practices or technologies. This can easily happen when staff are over-extended to the degree that they don’t have sufficient time to invest in further self-development or improvement. Finally, security teams typically have to deal with large volumes of alert metrics from security tools, causing alert-fatigue. This can place the organization at further risk of cyberattack or data breach.
SOC automation can help overcome all of these challenges. By automating manual SOC processes, organizations can keep up with emerging threats while protecting their systems, intellectual property, people, and data.
Whether your organization has a SOC or is considering adopting SOC automation, we hope you find this resource useful.
SOC automation can deliver benefits for many use cases related to enterprise security. Seven good examples are:
| Use Case | Description |
|---|---|
| Reduce false positives | Improves incident detection and minimizes alert fatigue |
| Triage threat analysis | Speeds up effective incident response and threat remediation |
| Analyze the threat landscape | Detects existing and emergent threats to continually protect the organization |
| Prevent lateral movement | Creates user containment workflows to prevent attackers from misusing stolen credentials for lateral movement |
| Isolate threatened endpoints | Quarantines infected endpoints and prevents threats from spreading across the network |
| Automated threat hunting for APTs | Initiates automated response workflows to neutralize threat actors before they reach the persistence stage |
| Gamify security training | Provides hands-on simulations and exercises to engage users and improve cyber hygiene |
SOC automation refers to automating the basic workflows, processes, and activities in a security operations center. Automated workflows that manage routine cybersecurity activities are paired with professionals who take overall responsibility and provide manual intervention.
With the right tools in place, SOC automation enables organizations to:
It’s important to keep in mind that SOC automation does not mean the total automation of the SOC. Rather, it is about automating specific tasks and processes to increase SOC effectiveness. Some common SOC activities that are simple to automate include alert analysis, compromised credential containment (e.g., password resets or blocks), incident analysis and response, and threat detection and triage.
Automating tasks such as these increases the speed, reliability, and ease of threat monitoring and detection process. It also helps to complement and augment human skills, enabling security teams to focus on challenges where decision-making abilities are required.
Security teams use SOC automation tools to streamline processes such as threat detection, monitoring, remediation and prevention. Two main tools play a key role in making this happen – security information and event management (SIEM) and security orchestration automation and response (SOAR).
A SIEM platform automatically collects and correlates security data from a range of sources, detects abnormal behaviors, and flags threats. Administrators can assess SIEM alerts and take appropriate action before significant damage is caused. SIEM plays an important role in cybersecurity visibility and SOC automation. However, its capabilities are limited to data aggregation, correlation and alerting.
Despite the usefulness of SIEM systems, security teams have to review, prioritize and act on these alerts manually. As organizations face an increasing number of threats, they seek solutions to automate alert analysis, prioritization and incident response. This is where SOAR comes into play.
With SOAR, organizations can do more than just collect threat-related data from different sources. They can correlate and enrich existing SIEM alerts and initiate adaptive response workflows to identify real threats. SOAR also improves response prioritization, speed, and proactively protects assets. All of this happens automatically and continuously.
That said, SOAR is not a replacement for SIEM. Rather, the two platforms work together to enable SOC automation. When implemented in a complementary fashion, SIEM and SOAR can reduce the time and cost of threat analysis and incident response by a significant margin. Ultimately, these tools empower organizations to reinforce their cybersecurity defenses.
SOC automation is suitable for a wide range of scenarios and, as we highlighted in our executive summary, this article aims to cover seven of the most common. To add extra detail, we will also provide practical examples.
SOC automation solutions enrich the quality of security alerts with important contextual information. This can help reduce mean time to detect (MTTD) and accelerate the mean time to respond (MTTR). These platforms also automatically weed out false positives to minimize alert fatigue and prevent burnout. This enables security teams to focus on real threats rather than wasting time and effort on false alarms.
Example:
An alert could be raised when a user mistypes an account password more than three times. Since the system has set three attempts as the maximum allowable limit, it may misconstrue the additional attempts as a brute force attack.
SOC automation can augment these alerts (and others) with helpful information such as geo-IP lookups and domain analysis. Equipped with this information, it can differentiate between a real security threat and a false positive. In our case the incident is a false positive, so no further action is needed.
Automated SOC tools can assess and validate different event types and quickly initiate appropriate responses. Without automation, analysts have to manually review alerts and divert their attention to investigate firewall logs (among other things) to assess and neutralize the threat.
Example:
At 2:00 p.m. on a Wednesday, the organization’s security tools detect two types of security event: A port scanning activity from an unknown IP address and an ongoing distributed denial of service (DDoS) attack.
While both events need to be investigated and stopped, they require different responses in terms of approach and urgency. The port scanning activity is classified as low priority and therefore doesn’t merit an immediate response. This will remain the case unless the reputation of the source IP is known to be bad or there have been multiple attempts from this IP address in a short time period.
A DDoS attack on the other hand can cause serious business disruption and result in huge losses. With SOC automation in place the malicious source IP addresses will be automatically and immediately blocked, preventing the sending of further malicious traffic
SOC tools can use AI to continually analyze an organization’s threat landscape. They are able to find and correlate existing and emerging threats, and to predict what impact these could have on the company and its assets. This information can also be used to create risk profiles and to inform strategic security decision making.
Example:
Malware, ransomware, phishing and supply chain threats are already well known to cybersecurity teams. However, new threats are constantly emerging or “upgrading” such as malvertising, cryptojacking and ransomware-as-a-service (RaaS). It is therefore crucial that security teams keep abreast of new malware and penetration techniques. Unfortunately, the rapid and diverse nature of these threats means that manual research is largely impractical.
However, an organization could deploy AI-based tools that continually review the threat landscape. These tools are trained using security models that enable them to understand the characteristics of malware and viruses. The trained AI solutions are now able to identify suspicious behavior within network traffic, data flows and systems. As a result, they will know if an unauthorized user is using software such as Coinhive to mine cryptocurrencies using corporate resources. If a cryptojacking attempt of this type is detected, a specific workflow counter measure can be initiated.
According to Verizon’s Data Breach Investigations Report (DBIR), stolen user credentials were responsible for 61% of all data breaches in 2021. SOC automation tools can create user containment workflows that prevent attackers from misusing stolen credentials. They also allow analysts to quickly block all access points from a compromised user, reducing MTTR and containing possible damage.
Example:
The privileged credentials of a mid-level manager are stolen via a rainbow table attack. The hacker attempts to use these credentials to log into the user’s (sensitive) account. Their goal is to establish a long-term presence in the account.
An automated SOC tool flags the hacker’s activity as suspicious. It uses machine learning to create a baseline of normal behavior and compares any new activity with this baseline. It determines that the hacker’s attempt to remain within the network using an authorized user’s credentials is suspicious and initiates a user containment workflow to reset the user’s password or block all access points from them.
Network endpoints are vulnerable to many threat actors and vectors, including malware and ransomware. Automated tools raise alerts about infected endpoints, which can then be quickly disconnected and quarantined preventing further spread.
Example:
An employee is working remotely and connecting to the enterprise network via an insecure Wi-Fi access point. A cyberattacker manages to gain control of the user’s device and installs malware.
An automated endpoint detection and response (EDR) tool would recognize the vulnerable endpoint and generate a critical alert. More importantly, it will also disconnect the compromised endpoint from the corporate network. Since it doesn’t wait for any human intervention it reduces both the response time and time to qualify (TTQ).
Threat hunting is a proactive way to find and mitigate against advanced persistent threats (APTs). However, this can be a time-consuming activity when performed manually. Automation decreases the time and effort required to hunt for these APTs. The tool initiates designated response workflows to neutralize threats before they have a chance to entrench themselves into the enterprise network.
Example:
A cybersecurity team collects a vast quantity of threat data from disparate datasets. But correctly analyzing this data is a time-intensive ongoing effort.
To simplify matters, the team could deploy automated tools such as extended detection and response (XDR) and anomaly detection platforms. With these tools they can collate threat intelligence reports from various sources. Whenever a new threat or exploit technique is discovered by the system, it will generate an alert.
Threat actors take advantage of poor cybersecurity hygiene and human carelessness to steal passwords, conduct social engineering attacks, gain unauthorized access to IT systems and so on. To close these human-created security gaps, training is essential. AI-based SOC tools can be used to gamify security training for security analysts (and other employees). Hands-on exercises and simulations can make this training more engaging and therefore more effective.
Example:
Microsoft’s Into the Breach exercise is a good illustration of gamified security training. During this exercise SOC analysts are placed into different teams and tasked with designing a defense strategy against AI-generated threats.
Unlike traditional training, where an instructor talks and a trainee listens, gamified lessons are more hands-on. This is also a great way of creating and fostering an organization-wide culture of security, outside of just the SOC.
Automated SOC tools can bring many benefits to an organization. But to maximize their benefit, it is important to have a thorough understanding of the day-to-day problems the SOC faces. Analyzing these needs first helps users select and implement the appropriate tool for the discovered problem domain.
After deployment, security admins should customize their SOC tools to address any specific need the business may have. Regular patching, upgrading and maintenance must also be conducted in order to meet evolving security challenges, ensuring long term efficacy.
It should also be noted that it is not the goal of automation to replace all human input, but to augment it. Even with automation in place, humans are required to make judgment calls, analyze new threats and neutralize novel attacks.
Another good practice is to support the SOC automation program with a strong security culture. Fostering a business-wide awareness of security means that each individual can play their part in defending against attack. Top-level leadership and corporate processes also should support and champion SOC automation.
The success of SOC automation also depends on how well it is documented, maintained and optimized. A centralized knowledge base of policies, documents and training materials should be available to keep everyone updated on current practices. This also can help the security team maintain systems and ensure that they deliver expected results.
Finally, it is often useful to work with an external managed security services provider (MSSP). These can be used to largely offload the management and optimization of the SOC and to provide measured results. Measurement is especially critical, as all security tools require constant adjustment for optimal function.
The SOC is the centralized “command center” from which systems and networks are monitored to protect them from malicious actors. However, modern SOC teams must cope with a constant and varied influx of threats and alerts, which often become overwhelming and increase the organization’s exposure to risk.
Automation can help minimize this risk by allowing SOAR and SIEM tools to take over day-to-day threat detection and response tasks. This helps reduce the burden on security teams and empowers the organization to beat the malicious actors at their own game.