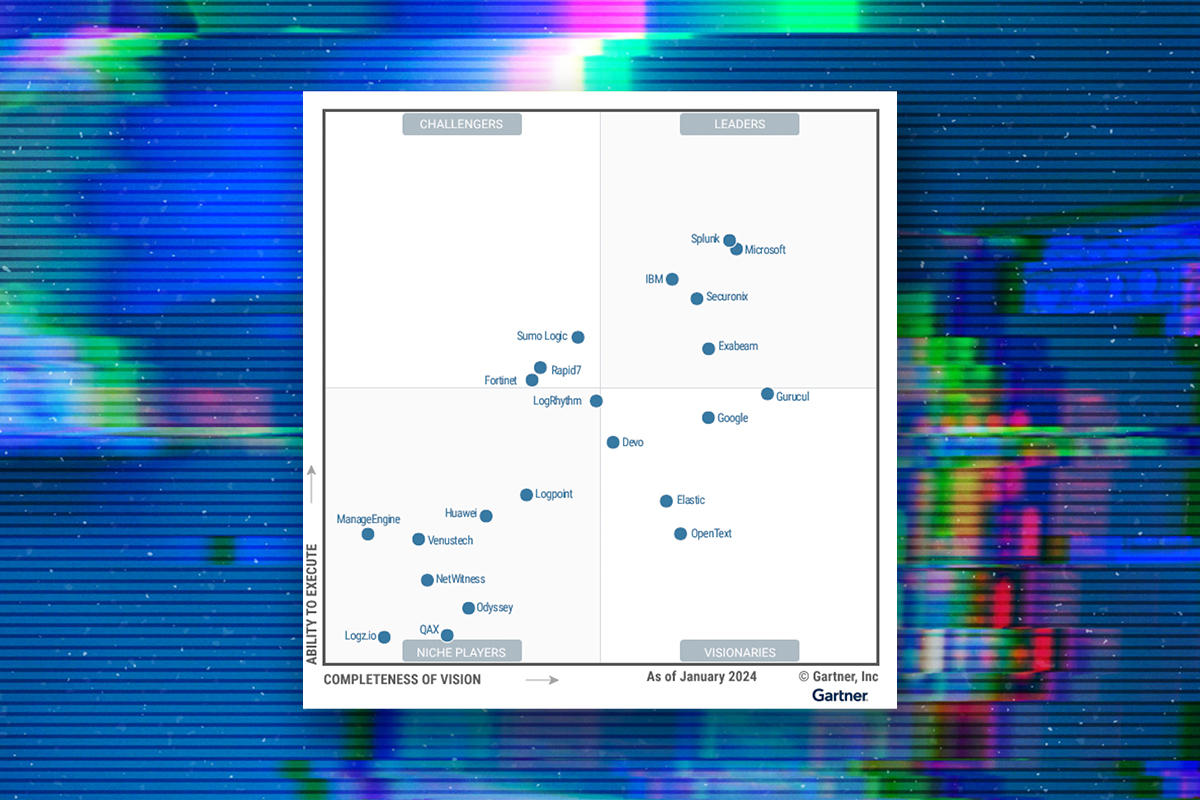
2024 Gartner Magic Quadrant for SIEM
Devo was recognized as a Visionary in the Gartner® Magic Quadrant™ for SIEM based on our Ability to Execute and Completeness of Vision.
The vulnerability management lifecycle is a cyclical and ongoing cybersecurity process of identifying, assessing, prioritizing, and addressing vulnerabilities in order to strengthen an organization’s cybersecurity posture.
This article details the vulnerability management lifecycle, and why it’s such a critical element of any organization’s cybersecurity program. It also highlights some best practices to help strengthen your organization’s vulnerability management program.
Below is an executive summary of the broad steps covered in a typical vulnerability management lifecycle process. We will explain these steps throughout the article.
| Discover assets | Prepare an asset inventory, and identify business-critical assets. This can also identify unauthorized assets or assets missed in asset management processes.Alongside, get organization-wide agreement on the need, objectives, and goals of the vulnerability management program |
| Prioritize enterprise assets | Prioritize assets based on the potential impact of a vulnerability’s exploitationAlso identify the key performance indicators (KPI) and other relevant metrics to report progress, measure success, and confirm if the program is delivering on its stated objectives |
| Find and assess vulnerabilities | Perform a vulnerability scan and penetration test |
| Prioritize and report vulnerabilities | Prioritize identified vulnerabilities based on potential impact and risk, prepare a detailed report |
| Address vulnerabilities | Address vulnerabilities based on priority |
| Verify remediation | Assess where remediation actions were successful |
| Continuous improvement | Maintain the cycle of excellence through feedback and continuous improvement |
A vulnerability is a cybersecurity weakness that a bad actor could exploit to gain unauthorized access to your enterprise network and compromise resources. The vulnerability could be present in unpatched or out-of-date software, or occur due to missing or weak authentication credentials. System misconfigurations, poor data encryption, malicious insider threats, injection flaws and zero-day vulnerabilities are some other, common types.
If an attacker successfully exploits a vulnerability, they can damage your organization in many ways. Here are a few examples:
One 2021 report revealed that 50% of internal application vulnerabilities were high-risk or critical-risk. Another study in 2020 revealed that a whopping 84% of companies had high-risk vulnerabilities on their external networks.
From these findings, it is clear that organizations need a way to proactively and continually identify, analyze, and remediate vulnerabilities. Here’s where a good vulnerability management program is beneficial.
The SANS Institute defines vulnerability management as a “process in which vulnerabilities in IT are identified and the risks of these vulnerabilities are evaluated. This evaluation leads to correcting the vulnerabilities and removing the risk or a formal risk acceptance by the management of an organization.”
Unlike vulnerability scanning, which is only about identifying vulnerabilities once, a vulnerability management program is about continuously assessing, prioritizing and remediating them. Moreover, the vulnerability management process is not a linear or one-time effort , but an ongoing lifecycle with multiple stages.
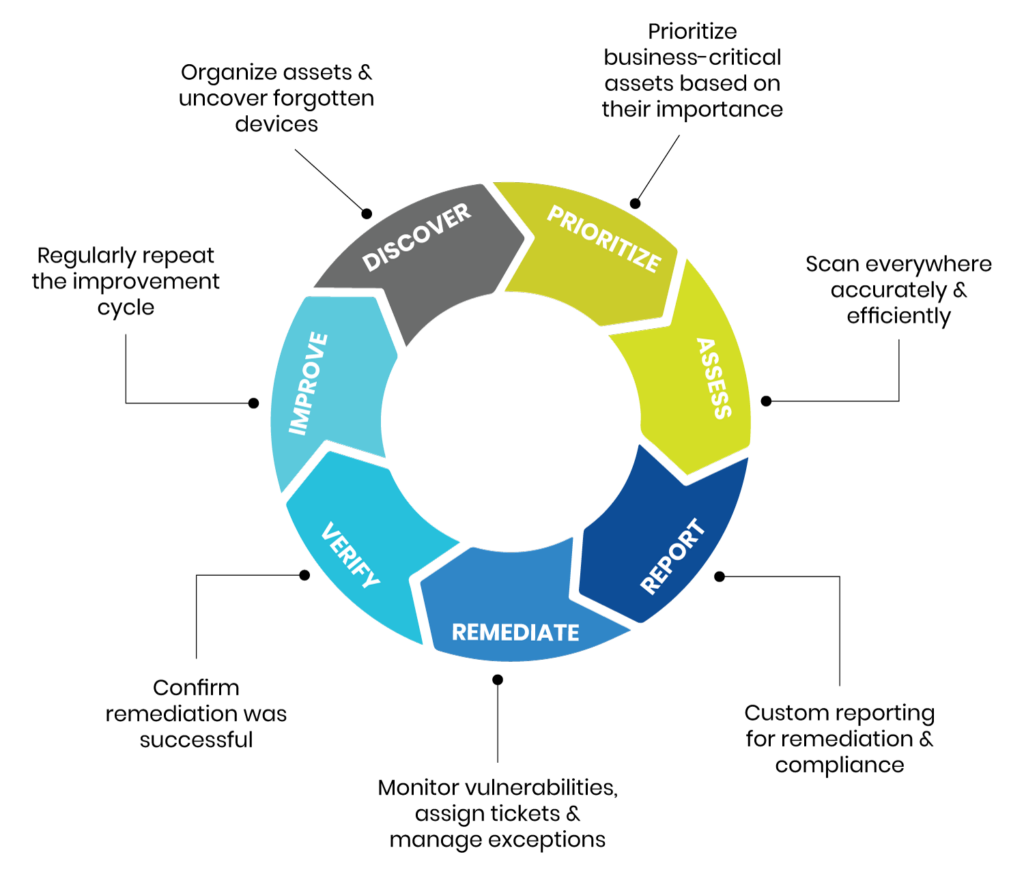
The vulnerability management lifecycle is an intricate cybersecurity practice that can help your organization find and fix security weaknesses before they can lead to an attack. It consists of 7 key stages.
The first step involves preparing an asset inventory – a list of all enterprise assets, such as devices, operating systems, software, and services that will be assessed for vulnerabilities. Make sure to uncover any forgotten or shadow IT devices. They may contain vulnerabilities that could harm the organization if left unattended or uncover unauthorized access (a new threat). Also, determine who has access to these assets and to what degree (read only, edit, move, etc).
Asset discovery is a method to help audit and potentially identify gaps in your asset inventories. The goal here is to have a fully defined scope of assets for your vulnerability management program and ensure that you are prepared for vulnerability scans and tests.
In this early phase, it’s also important to get organization-wide agreement on the need, objectives, and goals of your vulnerability management program. Buy-in at every level of the organization – from top management to the rank-and-file – will go a long way towards helping you streamline the lifecycle and meet the program’s goals.
Business-critical assets should then be prioritized based on impact and risk. Prioritization is crucial because it will help focus your vulnerability management efforts. Consider some of the following:
Prioritize assets that present the most significant risks if their vulnerabilities remain unidentified or neglected.
Before getting into the implementation phase, identify the key performance indicators (KPI) to report progress and measure the success of your vulnerability management program. Quantifiable metrics make it easier to understand if the program is delivering on its stated objectives, and helping the organization to address vulnerabilities and strengthen its cyber defenses. If it’s not, you can identify and implement actions to bring it back into alignment.
Now that you have an asset inventory, perform a vulnerability scan to find any vulnerabilities that may result in a breach, including:
Select a tool that can perform both authenticated (credential-based) and unauthenticated (non-credential-based) scans to find different types of vulnerabilities. Ensure that the tool can effectively differentiate between true positives (real vulnerabilities) and false positives (vulnerabilities that appear real but are not). This will minimize the burden of assessment, verification, and remediation on the security team.
Additionally, the tool should include threat intelligence capabilities such as identifying if the vulnerability is actively exploited in the wild or if a known exploit exists for the vulnerability. The tools should also be able to provide remediation steps and distinguish vulnerabilities where no known remediation is available. This information should be a factor in determining the prioritization of remediation.
Once you have discovered assets that are potentially weakened, prioritize the identified vulnerabilities based on potential impact: high-impact, medium-impact, and low-impact. Leverage threat intelligence to add context to vulnerability and threat data, and move from a reactive to a proactive stance in your fight against threat actors. Effective prioritization and threat intelligence enrichment will allow you to focus remediation efforts using fewer resources.
Compile all this information into a report that outlines:
Include clear instructions to inform the remediation team what actions to take in order to address vulnerabilities and decrease risks.
Before you start addressing vulnerabilities, prepare a plan of action with a list of activities, remediation owners, and important milestones. Track progress to confirm that the remediation effort is appropriately focussed and on-track. Also, perform root cause analyses to expand your knowledge of the vulnerability landscape and improve your vulnerability management program.
With a prioritized vulnerability list, decide whether you should:
Accepting the risk is often feasible for non-critical assets, or if the threat of exposure is low. Delaying remediation may not be ideal, but may be necessary when calculating risk and impact against other competing projects or priorities in the organization. Mitigating a vulnerability won’t completely eliminate the risk of exploitation, but it will reduce the likelihood and minimize potential damage. Always aim to remove a high-risk vulnerability, particularly if it affects a business-critical asset.
The assessment stage will reveal whether your remediation actions were successful and to what extent. This stage often includes a rescan of the remediated assets affected by the vulnerability. It should also reveal how successful your efforts were at:
At this stage, you should report key metrics back to senior management. This will help them better assess the company’s security posture and enable them to make decisions about new security investments.
Since vulnerability management is a cycle, feedback and continuous improvement are critical to maintain effectiveness. Look for ways to improve your security controls, policies, and procedures.
Research ways to strengthen weak defenses, and proactively defend the organization from both existing and evolving vulnerabilities.
To get the best possible value from your organization’s vulnerability management lifecycle, follow these best practices:
Regularly scan all devices that could act as an access point for cyberattackers or contain sensitive or confidential data. Ongoing scanning will reveal new vulnerabilities and help implement remediation plans that minimize risk.
Assigning an owner to each asset will increase accountability in your vulnerability management program. Asset owners should be responsible for patching and maintaining that asset, keeping it safe and operational.
Document all vulnerability scans and results. Robust documentation can help you track important trends, maintain activity trails, and improve cybersecurity training programs.
The IT team must be able to mitigate or remediate identified vulnerabilities in assets. Therefore, it is important to provide training on secure coding best practices and continuous security assessments.
Define key performance metrics and regularly review whether existing vulnerabilities and risks are being addressed. Use this information to redefine your security baselines, improve security training, and fine-tune your vulnerability management tools.
Leverage the output of your vulnerability scanner to enrich data in other tooling such as your SIEM or NDR. This enrichment can help provide value to other security functions.
Automate scanning and asset management processes whenever possible. In some instances, the scanning data can be used in conjunction with other solutions to provide automation in remediation (e.g. applying a patch that was missed or taking a system offline for a critical vulnerability).
Even if your company has never been attacked, keep in mind that new vulnerabilities and exploits are emerging every day, so it is no longer a matter of if, but when. This is why robust vulnerability management is a vital component of your overall cybersecurity program. It empowers you to improve your awareness of cybersecurity vulnerabilities, remediate weaknesses in your assets, continually maintain strong cyber defenses, and make informed decisions.