
eBook Journey to the Autonomous SOC
Unlock the power of automation. Discover the key factors for automating threat detection, hunting, and response in this ebook.
In the world of cybersecurity, an ounce of prevention is worth a pound of cure. By watching out for certain Indicators of Compromise (IoC), your organization can detect malicious threats to its network and quickly counter-attack, removing the threat and minimizing damage.
IoCs are digital forensic fingerprints – also known as “breadcrumbs” – that allow cybersecurity teams to detect, investigate and stop malicious activities and breaches. With this actionable threat intelligence, your security teams can stop in-progress attacks, isolate suspicious items, and prevent future incidents.
However, there are countless IoCs that can highlight security problems in your environment and selecting the important ones is not always easy. To help, this article will explore seven examples of IoCs that could suggest your enterprise network is compromised. For convenience, we have included an executive summary of these IoC examples and will cover each one in more depth as we progress.
| IoC | Description |
|---|---|
| Unusual outbound network traffic | Unusual outbound traffic patterns may indicate a potential attack |
| Unexplained activity using privileged account credentials | Privileged account escalations may indicate a malicious user trying to access sensitive data |
| Activity from unusual or unexpected geographical areas | Activity may indicate a cybersecurity threat from a different country |
| Sudden increase in database reads | Increases may mean an intruder has penetrated a database to exfiltrate data |
| Repeated requests to access the same file | May point to a malicious user trying to steal the file |
| Unusual or suspicious registry changes | Unexpected changes may indicate a malware infection |
| Large size of HTML responses | Could indicate an SQL injection to extract sensitive data from web applications |
An IoC could best be described as “evidence showing that an enterprise network has been compromised”. If a suspicious activity or malicious event is detected on a network, investigators will gather data in the form of IoCs for later forensic analysis. This is not unlike what CSI teams do when investigating bank robberies and homicides.
Thus, IoCs enable investigators to understand exactly what happened, where and how. This information can then be used to reduce the impact of the attack and to create tools that detect similar events in the future. For these reasons, IoCs are a useful addition to any enterprise cybersecurity program.
It should be noted however, that monitoring IoCs is a reactive exercise. This is because investigators are addressing events that have either happened or are happening. An approach based solely on IoCs will therefore be unable to discover many forms of evolving threat, including zero-day exploits and malware-free intrusions.
For robust and reliable security, organizations will therefore need a more proactive detection approach. This requires an understanding of the attacker’s intent and their methods, which is where Indicators of Attack, or IoAs, come into play. IoAs are based on behaviors that indicate an attack not covered by an IoC.
IoAs allow security teams to understand not only what is happening, but why it’s happening. This approach enables security teams to discover threats in near real-time and act immediately. Please note that an in-depth discussion of IoAs is beyond the scope of this article, but please feel free to find further details here.
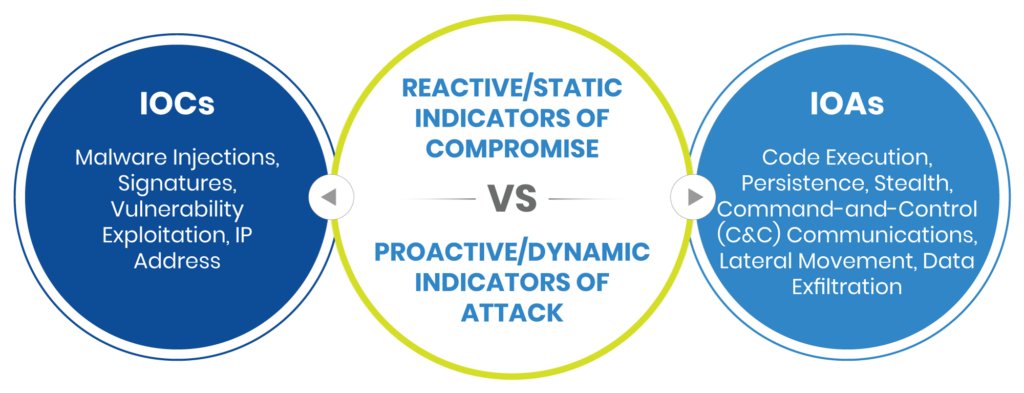
Image shows that IoCs are reactive where IoAs are proactive (Source)
Here are seven examples of IoCs that should be tracked as part of your cyberdefense strategy:
Excessive or unusual network traffic leaving your perimeter may indicate that an endpoint is infected with spyware. Spyware may be communicating with some form of command-and-control (C&C) server, allowing cyberattackers to steal data and move laterally across the network.
Fortunately, it is relatively straightforward to detect these unusual outbound traffic patterns. Packet sniffer tools – also known as network analyzers or network sniffers – intercept, log, and analyze network traffic. With these tools, you can identify unusual traffic patterns and pinpoint the cause of performance problems. Once detected, the key is to react quickly, reducing data loss and the likelihood of further compromise.
Image shows a common packet sniffing tool. Source
Privileged accounts provide elevated access and permissions to users, processes, and systems. They allow account-holders to perform sensitive and restricted actions, such as modifying or deleting files, adding or removing users and modifying user access to resources.
Cyberattackers can steal privileged account credentials by logging keystrokes or by cracking passwords through brute force. They may also trick privileged users into providing credentials via social engineering such as phishing. Once equipped, criminals can easily conduct account takeovers and steal sensitive data.
This IoC may show an external user trying to escalate the privileges of an account, or using a privileged account to access others. To monitor for this type of activity, use a robust Privileged Access Management (PAM) solution. You should also follow the Principle of Least Privilege (PoLP) and limit access rights, reducing the possibility of credential abuse.
If a lot of traffic is being generated from a region that typically doesn’t, this might indicate an unauthorized or malicious user on your network. For example, if your authorized network traffic generally originates from the United States or India, but you observe several login attempts emanating from Russia or China, it may be a valid indicator. Investigative steps should now be taken before serious problems occur.
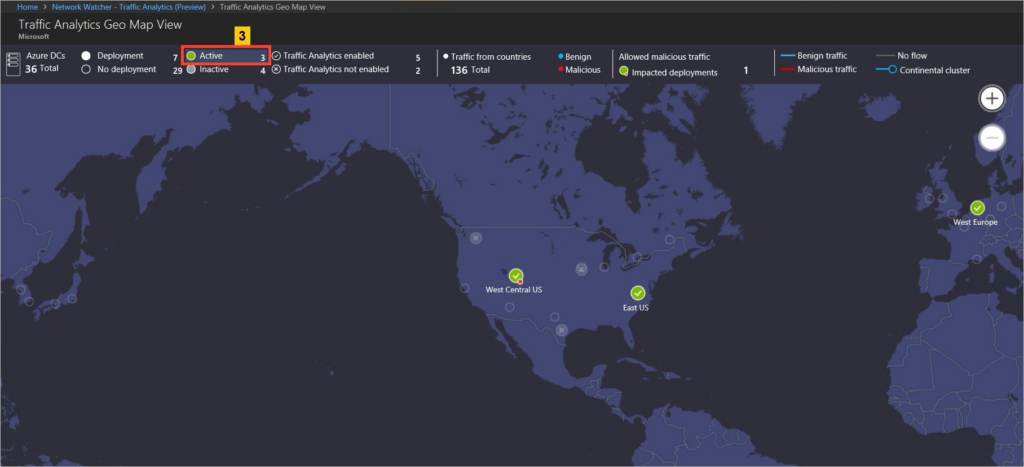
Image shows a traffic analysis tool displaying network traffic by region. Source
Substantial increases in database reads can be the result of an intruder penetrating your database systems. For example, if an attacker were to access a database containing thousands or millions of customer records, it would involve a request that generates read levels substantially higher than usual. If left unchecked, attackers could exfiltrate or make changes to data that negatively impact your business and reputation. It is therefore important to routinely monitor database activity for non-typical read requests.
It often takes trial-and-error before threat-actors can find an attack vector (point of entry) that allows them access to sensitive files. One possible IoC is where unauthorized users attempt to access the same file via multiple mechanisms. For example, someone might use multiple attack strings to access a file, such as “anyfilename.php” in order to compromise a vulnerable PHP web application. A high volume of requests, focused on a specific file, should raise suspicion and encourage investigation.
Malware is a persistent problem because it can establish itself in your network by making operating system registry changes. By modifying the registry, malware code can launch startup processes or store operational data that persist even after system reboots. If you see unusual registry changes, consider it an IoC that must be investigated. To assist with these investigations, establish a baseline registry snapshot of what a “normal” registry looks like. This can help you monitor the registry and quickly identify unauthorized or malicious changes.
An unusually large HTML response size may point to an SQL injection. This allows attackers to extract large amounts of sensitive data from web applications. For example, the typical size of an application query might be 100 KB. However, if an attacker has successfully executed an SQL injection attack, it may result in a much larger response size, perhaps 10 MB. If you notice abnormally large HTML response sizes, review the web application and investigate if it has been attacked via SQL injection.
Keep in mind that there are many other IoCs you can – and should – track. For help expanding your organization’s list of IoCs, take a look at the articles here and here.
While we have discussed seven key IoCs in this article, they do not represent an exhaustive or exclusive list. The threat field is constantly evolving and there are many other indicators that should be monitored and investigated. For example, look out for mismatched traffic between ports and applications, or large spikes in DNS requests. Also, monitor excessive failed login attempts on non-existent accounts or from employees that appear to be working after hours.
Finally, it is important to keep in mind that IoCs should not be the only weapon in your cybersecurity arsenal. Don’t forget, IoCs are reactive and should therefore be used in conjunction with their proactive partner, the IoA. More importantly perhaps, ensure that IoCs and IoAs are both used as part of a broader defense-in-depth strategy. When they are, threats to your enterprise networks can be minimized and your corporate assets can be protected from the bad guys!