
According to Research and Markets, the worldwide digital forensics market will expand at a compound annual growth rate of 13% through 2026. The rise of cybercrime is most certainly driving its growth — especially since digital forensics plays a critical role in mitigating cyberthreats in the modern security operations center (SOC).
So, what exactly is digital forensics? According to the National Initiative for Cybersecurity Careers and Studies, digital forensics collects, processes, preserves, analyzes and presents computer-related evidence to support network vulnerability mitigations. Your SOC analysts need visibility into the IT infrastructure, fast query speeds and accurate security alerts to conduct effective digital forensics and incident response (DFIR). Let’s take a look at how to start an investigation.
Digital Forensics Techniques and Procedures
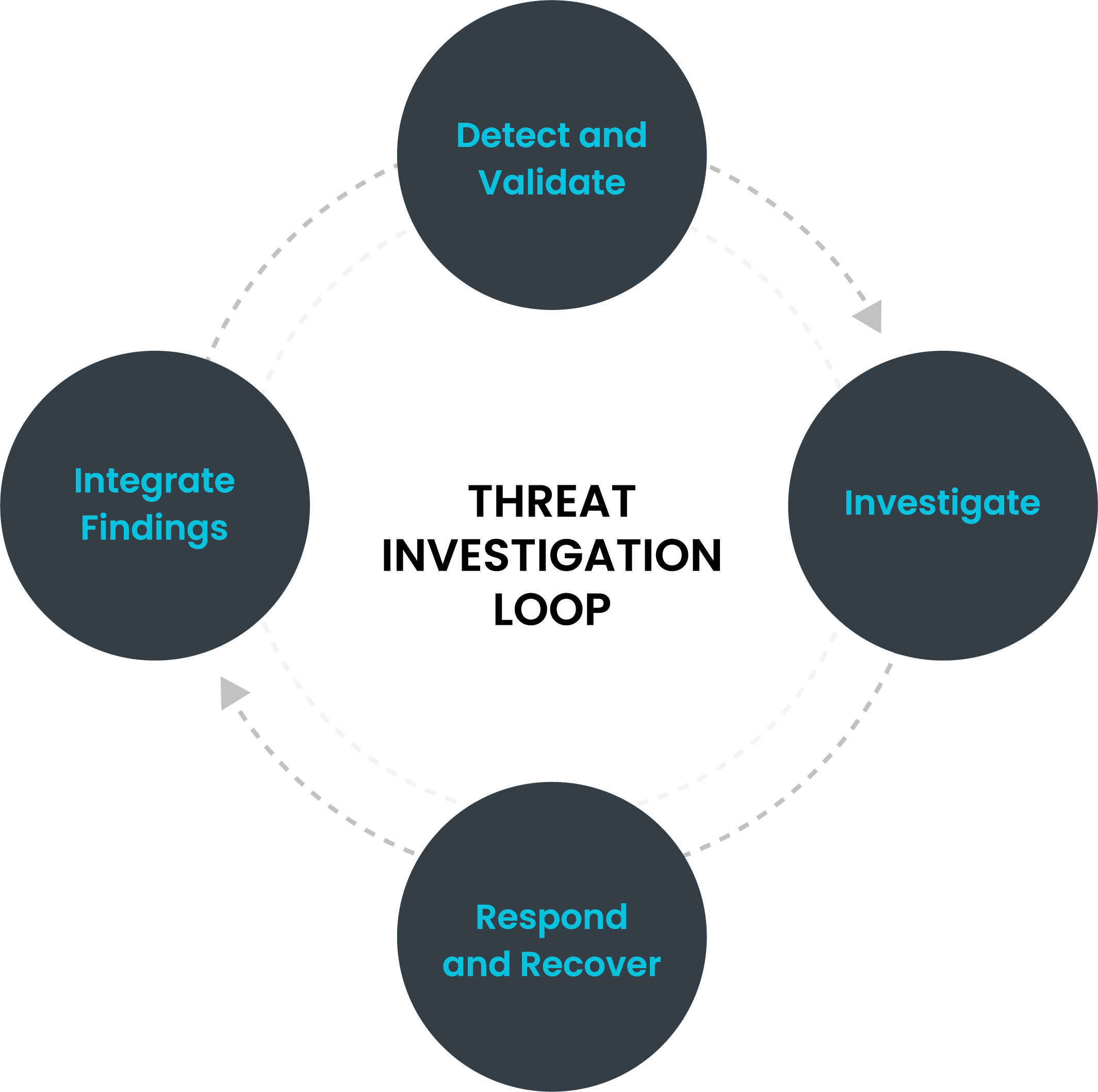
SOC analysts must follow four steps to conduct a successful digital forensics analysis so they can determine the correct response to a security incident:
- Gathering relevant evidence: SOC analysts must draw from different data sources to collect evidence related to a security event. Evidence can include network, web, access, IDS data and more. To enable SOC analysts to do this, companies should consider adopting a security solution that empowers analysts to quickly access, correlate and analyze real-time and historical data at scale.
- Enriching data with contextual intelligence: SOC analysts also should enrich data with threat intelligence to gain accurate insights about historical and ongoing attacks. Behavior, computer, atomic indicators, and descriptive tactics, techniques and procedures (TTP) can help your SOC analysts track, observe and understand indicators of compromise.
- Pivoting, filtering and iterating: To stop ongoing cyberattacks, SOC analysts need to move fast. Having lightning-fast query speeds is critical in this effort. Your security solutions should enable SOC analysts to easily switch between different views and queries so they can answer complex questions with their data. Your SOC analysts must also be able to drill down directly into a log from an alert or visualize a threat path within minutes of detection. If they’re unable to move fast, it can spell disaster for your organization.
- Integrating lessons learned: Once a threat is resolved, your SOC team must take the necessary steps to prevent a similar cyberattack from happening in the future. History is always bound to repeat itself, so it’s best to be prepared. They should conduct an in-depth analysis to update incident response plans (IRP), preserve digital evidence for compliance and legal purposes, and integrate the new insights into existing workflows. Digital forensics is a cyclical process — if your security operations team doesn’t incorporate what they’ve learned into their plans, then all their work will go to waste.
How Your Business Can Use Digital Forensics
As more workloads migrate to the cloud, the importance of DFIR will only grow. And as IT infrastructures expand and cyberthreats increase in sophistication, your security team likely will face challenges in monitoring and analyzing an ever-increasing volume of data. Vastly more data makes it difficult to distinguish between false-positive alerts and valid threats.
The fact of the matter is that legacy security tools simply cannot keep up with the modern threat landscape. However, the Devo Security Data Platform, a next-gen cloud SIEM, empowers your SOC team to conduct DFIR to protect your organization against cyberattacks. Devo helps improve your organization’s security visibility so analysts can detect and investigate threats more efficiently and effectively.
It also ingests data from all sources — in the cloud or on premises — and retains it for 400 days. Keeping historical data is critical when SOC analysts need to look back during an investigation. Further, alerts in Devo help monitor active queries on specific events and trigger real-time notifications for your security analysts to investigate. Analysts can triage alerts efficiently with just one click to automatically group them according to the entity or alert type, sort and filter alerts using their preferred method, and save them for future use. It also has a host of automation capabilities, making it even easier for your SOC analysts to conduct DFIR quickly and efficiently.




